Catenary v0.1
Mashle Burneded
Geass Labs
mashle@geasslabs.xyz
April 2025
Abstract
We're introducing Catenary, a fresh take on modular financial market infrastructure. It's built as a specialized Layer 3 network using the OP Stack. Catenary aims to solve major problems in clearing and settlement of cross-border trades within Sub-Saharan Africa. By using distributed ledger technology, it helps money flow more smoothly and efficiently between continents, which in turn speeds up economic and financial integration. At its core, Catenary includes a native Centralized Limit Order Book (CLOB) designed for high speed and almost instant transaction confirmation right on the L3. Our goal is super-fast settlement finality, achieved by using the Base Layer-2 along with Zero-Knowledge proofs. This combination should make finalization much quicker than traditional optimistic rollups. We've paired this with cost-effective data availability through EigenDA. A key piece of Catenary's design is Geass, an intent-based execution engine that handles complex coordination between off-chain and on-chain activities and guarantees settlement across different systems. The network also features a Proof-of-Liquidity (PoL) mechanism, carefully crafted using mechanism design ideas to encourage deep and sustainable liquidity. Another important innovation is Mobius, which represents an Agentic AI Council system built to bridge the gap between decentralized infrastructure and traditional, state-owned systems. Mobius acts as a technical gateway, making fiat on/off-ramping easy and helping Catenary work with various older systems. Catenary also supports the creation of programmable, stable digital currencies backed by diverse reserves, including tokenized government debt. By bringing together an optimized L3 setup, a high-performance CLOB, new intent and liquidity mechanisms, advanced AI for interoperability, faster settlement using ZK proofs on L2, and a solid stablecoin design, Catenary presents a technically advanced solution for trading less common assets and achieving incredibly fast global settlements, heralding a new era of permissionless financial innovation.
Catenary: Redefining the Monetary Layer
1 Introduction
Moving money and facilitating trade across borders in Sub-Saharan Africa (SSA) faces significant hurdles, including fragmented financial systems, high transaction costs, slow settlements, and limited access to efficient payment methods. Compounding these challenges, even widely promoted innovations like stablecoins, while sometimes easing liquidity issues, risk driving dollarization, devaluing local currencies, and contributing to volatile inflation. These issues hinder economic integration, slow down business growth (especially for small and medium enterprises), and limit financial access for individuals. The traditional correspondent banking network, while established, often gets bogged down by multiple steps, complex regulations across numerous countries, and outdated technology, leading to delays and unpredictable fees. While distributed ledger technologies offer potential solutions, existing general-purpose blockchains often struggle with the speed, latency, and cost requirements needed for high-frequency financial market operations and smooth integration with diverse existing systems, including state-owned financial infrastructure.
Catenary is envisioned as a transformative solution designed to tackle these critical challenges directly. By harnessing the capabilities of distributed ledger technology, Catenary aims to accelerate and simplify cross-border trade clearance and settlement, fostering an environment ripe for enhanced economic and financial integration. Our mission is to enable the seamless, efficient, and secure flow of payments and asset transfers, reducing friction and unlocking new opportunities for participants across the continent and globally.
At its core, Catenary is structured as an application-specific Layer 3 network built upon the OP Stack, settling transactions on the Base Layer-2. This architecture provides the ideal environment for optimizing performance, potentially customizing gas economics, and tailoring features specifically for financial market use cases. This approach overcomes the limitations that general-purpose L1s or L2s face in this specific application domain. Within this L3 environment sits a native Centralized Limit Order Book (CLOB), engineered for superior speed, throughput, and capital efficiency compared to decentralized automated market makers (AMMs), particularly for trading patterns involving limit orders and specific price levels.
Crucially, Catenary employs innovative technical mechanisms to achieve its objectives. Geass abstracts away transactional complexities, enabling sophisticated off-chain computation while guaranteeing on-chain settlement through a verifiable and transparent process. This facilitates seamless integration between decentralized applications and traditional payment flows. To ensure deep and reliable liquidity, the network utilizes a novel Proof-of-Liquidity (PoL) mechanism, designed with careful consideration of economic incentives to align the interests of liquidity providers and network participants. Furthermore, Catenary facilitates accelerated settlement finality: while transactions confirm almost instantly on the L3, final settlement leverages the robust security of Base Layer-2. The finalization process is significantly expedited through the integration of Zero-Knowledge proofs, reducing the time required for Layer 1 assurance compared to standard optimistic rollup withdrawal periods.
A cornerstone of Catenary's vision for broad interoperability is the Mobius Sybil Agentic Council (MSAC). MSAC is specifically engineered to act as a sophisticated technical interface. It leverages agentic principles to bridge communication and transaction execution between the decentralized Catenary L3 and diverse external systems, including legacy traditional financial infrastructure and state-owned servers. This unique AI-driven layer enables seamless fiat on/off-ramping and allows Catenary to integrate deeply with existing financial ecosystems, overcoming a major hurdle in the adoption of decentralized finance for mainstream and institutional use.
Catenary also supports the creation and utilization of programmable, stable digital currencies. These currencies are designed for stability through a diversified reserve model that may include major digital assets and tokenized sovereign debt instruments from participating nations, offering both reliability and enhanced functionality for financial programming.
This paper presents a detailed technical description of the Catenary network. We contribute:
- A novel application-specific Layer 3 architecture on the OP Stack optimized for financial market infrastructure.
- The design and implementation of a high-performance native CLOB within an L3 execution environment.
- The formal definition and technical workings of Geass for off-chain/on-chain coordination and guaranteed settlement.
- The mechanism design and analysis of the Proof-of-Liquidity (PoL) protocol, including quantitative validation via simulation.
- The technical architecture and function of the Mobius Sybil Agentic Council for heterogeneous system interoperability and fiat gateway services, including performance analysis via simulation.
- An outline of the programmable stable digital currency design and reserve mechanism, including stability analysis via simulation.
- An analysis of Catenary's performance potential (throughput, latency, cost, finality) via simulation and security considerations across the stack.
By detailing these technical components, this paper aims to provide a comprehensive foundation for understanding Catenary's innovative approach to building a hyper-performant, interoperable, and efficient settlement infrastructure for Sub-Saharan Africa and beyond.
2 Background and Related Work
Efficient and cost-effective cross-border financial transactions are fundamental enablers of global commerce and economic development. Despite advancements in financial technology, significant friction persists, particularly in emerging markets. This section reviews the existing landscape, covering both traditional and nascent blockchain-based approaches, and outlines the technical concepts relevant to Catenary's design.
2.1 Cross-Border Payments: Traditional Systems and Limitations
The dominant paradigm for international financial transfers relies on a network of correspondent banks. This system involves a series of bilateral relationships where banks hold accounts with each other to facilitate transfers on behalf of their clients. While robust and globally established, this architecture is inherently multi-hop, meaning a payment from bank A in country X to bank B in country Y may traverse several intermediary banks.
Technically, this multi-hop process leads to several inefficiencies:
- Increased Latency: Each intermediary bank adds processing time, resulting in settlement cycles that can span days. This delay ties up capital and introduces uncertainty.
- High and Opaque Costs: Each correspondent bank in the chain typically charges a fee, making the final cost to the end user unpredictable and often excessive, especially for smaller transactions. Fees for currency conversion at each hop further compound this issue.
- Operational Complexity: Managing multiple correspondent relationships across diverse jurisdictions is complex and resource-intensive for financial institutions.
- Limited Transparency: The lack of real-time visibility across the entire payment chain makes tracking difficult and resolving issues protracted.
- Capital Inefficiency: Banks must pre-fund nostro/vostro accounts in various currencies to meet payment obligations, tying up significant capital globally.
For regions like Sub-Saharan Africa, these issues are often exacerbated by less developed financial infrastructure and a greater number of currency pairs requiring multiple conversion steps. The reliance on a fragmented network hinders intra-regional trade and integration.
2.2 Blockchain-Based Financial Infrastructure: Evolution and Challenges
Blockchain technology, with its promise of disintermediation, transparency, and programmable settlement, has long been explored as a potential solution to the inefficiencies of traditional finance. Early initiatives focused on leveraging distributed ledgers for interbank settlement (e.g., R3's Corda, Hyperledger Fabric), often in permissioned environments to meet regulatory requirements and maintain control. While demonstrating improvements in speed and transparency within controlled networks, these often fall short of achieving broad, permissionless interoperability and rely on the participants being within the established consortium.
Public, permissionless blockchains like Bitcoin and Ethereum introduced the concept of truly open financial systems and programmable money (DeFi). Decentralized Exchanges (DEXs) built on these networks offer alternatives to centralized trading venues. However, these early public chains face significant challenges for high-frequency, high-volume financial applications like cross-border trade settlement:
- Scalability Limitations (TPS): Layer 1 blockchains often have low transaction throughput, leading to network congestion and high fees during peak demand.
- Latency and Finality: While transactions are broadcast quickly, achieving final, irreversible settlement on L1s can still take minutes to hours, which is insufficient for many real-time financial operations.
- Predictability of Fees: Transaction fees on busy L1s can be highly volatile, making cost planning difficult for businesses.
- Interoperability Gaps: Connecting permissionless blockchain networks with traditional financial systems and state-owned infrastructure remains a significant technical and operational challenge.
Later blockchain innovations, such as Layer 2 scaling solutions, have emerged to address some of these issues, providing the foundation upon which systems like Catenary are built.
2.3 Layer 2 and Layer 3 Scaling Solutions
To overcome the inherent scalability limitations of Layer 1 (L1) blockchains, Layer 2 (L2) scaling solutions have gained prominence. These technologies execute transactions off-chain in a more performant environment and periodically batch or commit the resulting state changes back to the L1. Optimistic Rollups, such as those built using the OP Stack, are a prominent L2 architecture. They operate by optimistically assuming that all transactions executed on the L2 are valid and submitting batches of compressed transaction data and state roots to the L1. Finality on the L1 is ensured through a fraud proof mechanism: a time window is provided during which participants can challenge the validity of a submitted batch by submitting a fraud proof to the L1, reverting invalid state transitions. This optimistic assumption allows for high transaction throughput off-chain but introduces a significant delay (the challenge period) before transactions achieve full L1 finality.
The OP Stack provides a modular framework for building Optimistic Rollups. Its design philosophy enables the creation of "superchains" and interconnected L2s. Extending this concept, Layer 3 (L3) networks can be built on top of L2s. An L3 can be application-specific, allowing for greater customization of the execution environment, gas token, governance, and feature set tailored to a particular use case. By settling onto an L2 (which in turn settles onto an L1), L3s can potentially offer higher throughput and lower transaction costs specific to their application compared to a general-purpose L2, while still inheriting the security guarantees of the underlying L1 (albeit with potential added latency for full finality depending on the proving and settlement mechanism). Catenary leverages this L3 paradigm on the OP Stack to create an environment specifically optimized for high-performance financial market operations.
2.4 Decentralized Exchange Architectures
Decentralized Exchanges (DEXs) enable peer-to-peer trading of digital assets without relying on a centralized intermediary to hold funds. Two primary architectures dominate the DEX landscape: Automated Market Makers (AMMs) and Centralized Limit Order Books (CLOBs).
- Automated Market Makers (AMMs): AMMs utilize liquidity pools and pre-defined mathematical functions (like the constant product formula
x*y=k) to determine asset prices and execute trades. Liquidity providers deposit pairs of assets into pools and earn trading fees. AMMs are generally simpler to implement on resource-constrained blockchains and provide continuous liquidity, particularly effective for token swaps. However, they can suffer from impermanent loss for liquidity providers and are prone to slippage, especially for large orders, and may not be ideal for precise limit order execution or complex trading strategies common in traditional finance. - Centralized Limit Order Books (CLOBs): CLOBs aggregate buy and sell orders at specific price levels in an order book. Trades are executed when buy and sell orders match on price and quantity. This is the standard architecture in traditional financial exchanges and many centralized crypto exchanges. Implementing a high-performance CLOB directly on a busy L1 blockchain is challenging due to throughput and latency requirements. Orders need to be placed, modified, and cancelled frequently, operations that are costly and slow on L1s. Some DEXs employ hybrid approaches, using off-chain order books with on-chain settlement, which introduces some degree of centralization risk depending on the off-chain component. Catenary's decision to implement a native CLOB within its application-specific L3 environment is a deliberate choice to provide a trading experience familiar to traditional finance users, enable precise price control via limit orders, and potentially achieve higher capital efficiency for concentrated liquidity, while benefiting from the L3's optimized performance characteristics.
2.5 Intent-Based Systems
Traditional blockchain interactions typically require users to specify precisely how they want a transaction to be executed (e.g., which function to call on which contract with which parameters). In contrast, intent-based systems focus on the user specifying what they want to achieve (their "intent"), leaving the execution details to a network of solvers or a dedicated protocol. This approach can significantly improve user experience by abstracting complexity and can potentially lead to more efficient outcomes by allowing specialized actors to find the best execution paths (e.g., optimal routing across multiple DEXs). Geass, as Catenary's core logic, is an intent-based design which allow users to express complex financial desires (like cross-currency settlement with specific constraints) and guarantee their settlement through the Catenary network.
2.6 Mechanism Design and Proof-of-Stake/Liquidity Concepts
Mechanism design, a field bridging economics and computer science, provides tools for designing rules and incentives to achieve desired outcomes in a system with self-interested participants. In decentralized systems, mechanism design is crucial for creating protocols that are robust, secure, and efficient, aligning individual incentives with the overall health of the network. Proof-of-Stake (PoS) consensus mechanisms are a prime example, incentivizing validators to act honestly through staked collateral. Proof-of-Liquidity (PoL), as conceived in Catenary, draws upon these principles. While not a consensus mechanism in the traditional sense, it is a mechanism designed to incentivize and coordinate liquidity provision by rewarding participants based on verifiable metrics of liquidity quality, aiming to ensure deep and stable markets.
2.7 Data Availability Solutions
A critical bottleneck for rollup scalability is the requirement for transaction data to be available so that anyone can verify the state transitions or challenge invalid batches. Posting all raw transaction data directly to the Layer 1 blockchain can be prohibitively expensive, limiting the cost-effectiveness of rollups. Data Availability (DA) solutions provide alternative, more cost-effective ways to ensure data is available without consuming expensive L1 blockspace. These solutions often involve dedicated networks or protocols that attest to the availability of data. EigenLayer's EigenDA is one such solution designed for rollups, leveraging Ethereum restaking for security. Catenary utilizes EigenDA to ensure the availability of its L3 transaction data in a cost-effective manner, crucial for maintaining verifiability while enabling high throughput.
2.8 Heterogeneous System Interoperability and Agentic Systems
Seamless interaction between disparate computing systems, especially across different trust domains and technological paradigms (e.g., decentralized networks, traditional databases, state-owned enterprise systems), remains a significant technical hurdle. Traditional APIs and middleware often struggle with the complexities of protocol translation, data format conversion, and managing asynchronous communication across systems with vastly different security models and operational assumptions. Agent-based systems, originating from artificial intelligence research, offer a paradigm for managing complexity through autonomous or semi-autonomous software entities (agents) that can perceive their environment, make decisions, and act to achieve goals, often coordinating with other agents. Drawing inspiration from principles of autonomous multi-agent coordination and robust inter-system communication, Catenary introduces the Mobius Sybil Agentic Council. This system is specifically engineered to act as a sophisticated technical interface, leveraging agentic principles to bridge communication and transaction execution between the decentralized Catenary L3 and diverse external systems, aiming to overcome the limitations of traditional interoperability approaches.
3 Catenary Technical Architecture
Catenary is architected as a modular, multi-layered financial market infrastructure designed for performance, cost-efficiency, and heterogeneous system interoperability. The core of Catenary resides on an application-specific Layer 3 (L3) network, built upon the robust and extensible OP Stack, which settles transaction batches to a Layer 2 (L2) chain (Base), ultimately inheriting security from the Ethereum Layer 1 (L1) blockchain. Data availability for the L3 is handled efficiently by leveraging EigenDA. Furthermore, a distinct but integrated component, the Mobius Sybil Agentic Council, facilitates critical interoperability with external traditional and state-owned financial systems.
3.1 Architectural Overview
The Catenary architecture can be visualized as a vertical stack with horizontal interoperability facilitated by MSAC.
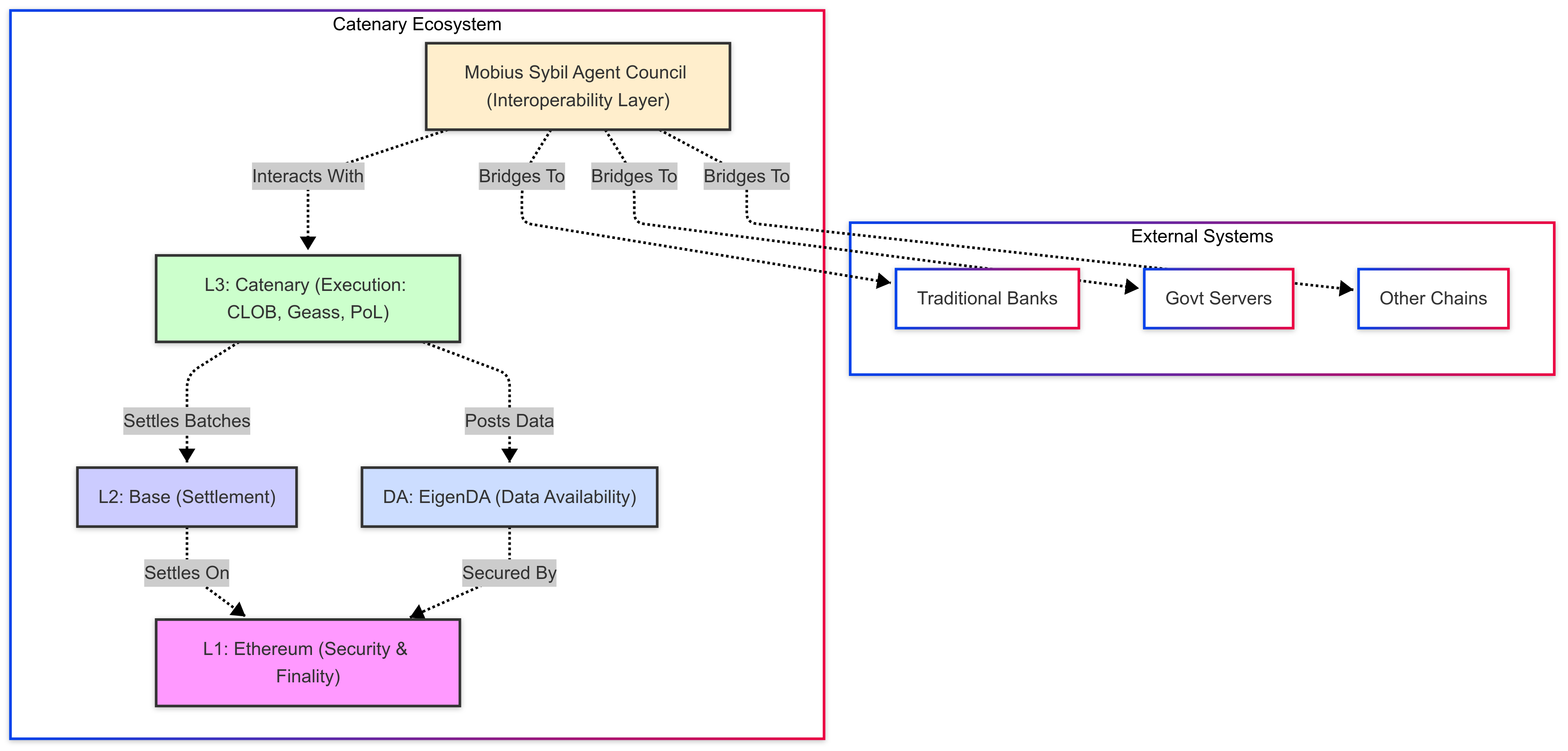
- Layer 1 (L1): Ethereum serves as the foundational security and finality layer.
- Layer 2 (L2): Base (an OP Stack L2) is utilized as the settlement layer for Catenary's L3 batches. This provides a balance of cost and speed compared to direct L1 settlement for L3 batches.
- Data Availability Layer: EigenDA provides a dedicated, cost-optimized service for publishing L3 transaction data batches, ensuring data availability necessary for verifiability and fraud proofs without incurring high L1 gas costs.
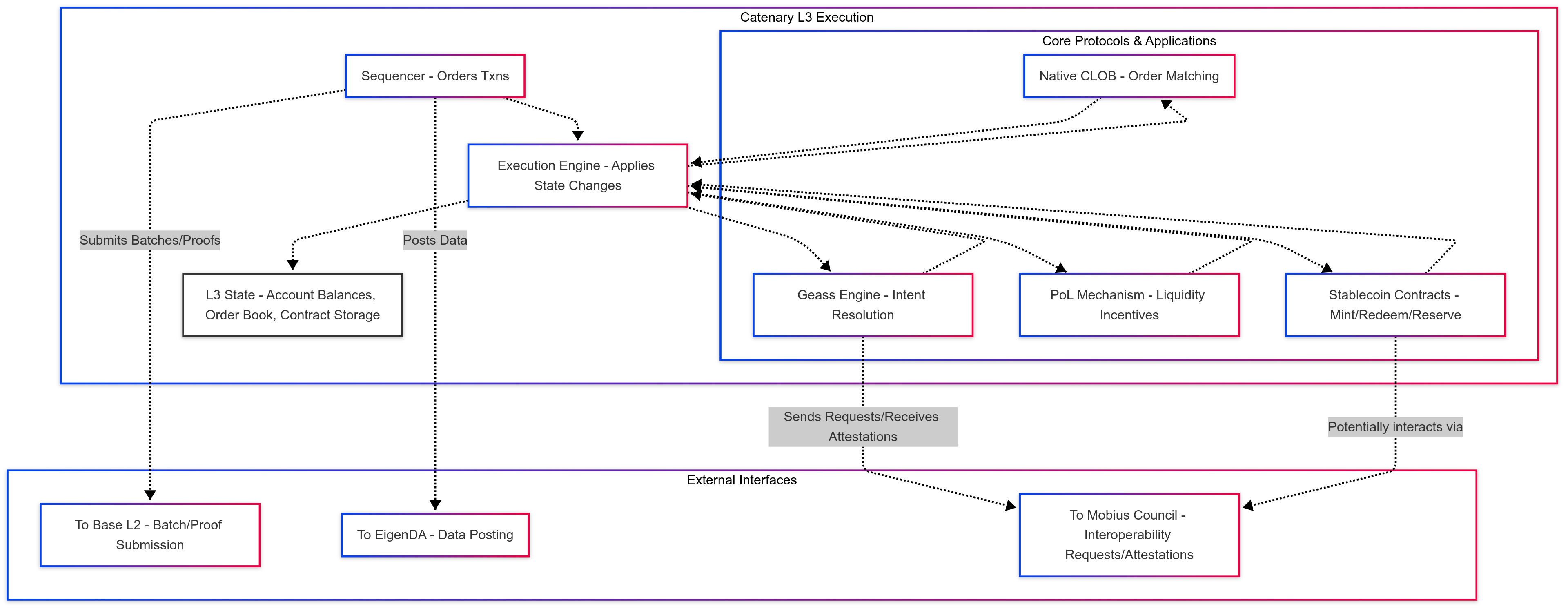
- Layer 3 (L3): The core Catenary execution environment. This is an application-specific rollup built on the OP Stack. It hosts the native CLOB, the Geass Intent Logic protocol implementation, the Proof-of-Liquidity mechanisms, and smart contracts governing the programmable digital currencies. This layer is optimized for the low-latency, high-throughput requirements of financial trading and settlement.
- Mobius Sybil Agentic Council: An off-chain (but securely integrated and potentially verifiable) system comprising autonomous agents coordinated by Geass. This layer acts as a technical middleware and gateway, interacting with the Catenary L3 via defined interfaces and communicating with external, heterogeneous systems (traditional banks, government servers, other blockchains) to facilitate functions like fiat on/off-ramping, data exchange, and protocol translation.
This layered approach allows Catenary to abstract the complexities of L1 security and L2 settlement while providing an environment highly tuned for its specific financial market application.
3.2 The Application-Specific Layer 3 on OP Stack
Catenary is deployed as a dedicated Layer 3 instance utilizing the OP Stack framework. The decision to build on Layer 3, rather than directly on L2, is motivated by several key technical advantages specific to the requirements of a high-performance financial market infrastructure:
- Application Optimization: L3s can be precisely tuned for their intended application. This includes:
- Custom Gas Markets: Catenary can implement a gas fee structure optimized for financial transactions, potentially using its native token or stablecoins for gas, providing predictable and lower transaction costs than typical L2s sharing blockspace with diverse applications.
- Tailored Execution Environment: The L3 execution environment can be optimized for the specific logic of the native CLOB and Geass protocol, potentially allowing for more efficient state access and computation related to order matching and intent resolution.
- Specific Features: The L3 can incorporate precompiled contracts or custom logic directly relevant to financial primitives, such as advanced order types or specific settlement logic, without competing for limited L2 blockspace or requiring complex L2 smart contract implementations.
- Performance Isolation: Running on a dedicated L3 isolates Catenary's performance from the activity of other applications on the underlying Base L2. High transaction volume on Catenary will not directly congest Base, ensuring consistent performance. Conversely, unrelated congestion on Base will not directly impact Catenary's internal transaction processing speed (though it would affect the speed of batch settlement to L2).
- Increased Throughput Potential: By offloading execution to a dedicated L3 with optimized parameters, Catenary can theoretically achieve significantly higher transaction throughput for its specific operations compared to running as smart contracts on a general-purpose L2.
- Future Flexibility: The modular nature of the OP Stack facilitates potential future upgrades or modifications to the L3's components (sequencer, execution engine, etc.) to adapt to evolving requirements or technological advancements.
The Catenary L3 maintains its own state, managed by a sequencer. Batches of L3 transactions and their corresponding state roots are periodically committed to the Base L2 contract. The security of the L3 relies on the integrity of the sequencer and the ability of participants to verify the posted data on EigenDA and challenge invalid state transitions via Base L2 (in an optimistic fraud proof model, or via validity proofs in a ZK-accelerated model, as discussed below).
3.3 Settlement Finality via Base L2 and Accelerated Proofs, and Data Availability
The security and finality of transactions executed on the Catenary L3 are ultimately derived from the underlying Base L2 and Ethereum L1. The Catenary L3 sequencer is responsible for collecting L3 transactions, executing them to produce new state roots, and periodically submitting batches of transaction data and state roots to a verification contract deployed on Base L2.
Traditional Optimistic Rollups rely on a fraud proof window for L1 finality, which can take days. Catenary aims to significantly accelerate this process to meet the demands of financial markets. While transaction confirmation on the Catenary L3 is designed to be near-instantaneous (providing users with immediate feedback and a high degree of probabilistic assurance within the L3 environment), achieving faster L1-based finality (final, irreversible settlement guaranteed by Ethereum's security) is crucial for bridging to other systems and ensuring robustness against potential L3-level issues like sequencer misbehavior.
Catenary employs a mechanism that combines the batch submission to Base L2 with the generation and verification of Zero-Knowledge (ZK) proofs. The L3 state transitions, as executed by the sequencer, are designed to be compatible with ZK proving systems. An independent network of provers (or a dedicated proving service) generates ZK validity proofs attesting to the correctness of the state transitions within each L3 batch. These proofs are then verified by a smart contract on Base L2.
The technical flow is as follows:
- L3 transactions are sequenced and batched.
- Transaction data for the batch is posted to EigenDA (detailed below).
- A state root update is proposed on Base L2.
- Concurrently, ZK provers generate a validity proof for the batch, confirming the state transition from the previous state root to the new one is correct according to the L3's execution logic and the posted data.
- The ZK proof is submitted to a verifier contract on Base L2.
- Upon successful verification of the ZK proof by the Base L2 contract, the L3 batch is considered finalized on Layer 2.
This ZK proof verification step allows Catenary to bypass the lengthy optimistic challenge period typically required by Base (as an Optimistic Rollup settling to L1). While achieving true L1 finality still depends on Base's own path to L1 finality, the ZK proof significantly accelerates the point at which the L3 batch's correctness is cryptographically guaranteed on L2, dramatically reducing the time to settlement finality from potentially days to a much shorter timeframe (measured in the range of seconds to minutes in simulation, see Section 6.3 Performance). The precise mechanism for integrating ZK proof generation and verification with the OP Stack's fraud proof system, or potentially migrating towards a ZK-hybrid model if supported by the underlying L2 framework, will be detailed in Section 9 (Future Work). The goal is to provide L2 finality guarantees within a window suitable for financial operations, bolstering the security of the near-instant L3 confirmations.
Data Availability (EigenDA):
Transaction data for each L3 batch sequenced by Catenary is published to EigenDA. EigenDA provides a scalable and cost-effective solution for ensuring this data is accessible off-chain. The use of EigenDA significantly reduces the data posting costs compared to publishing directly to Ethereum L1 calldata, enabling higher transaction volume on the L3 at a lower operational cost. The security guarantee of EigenDA, derived from Ethereum restaking, ensures that the data is available to anyone who needs to reconstruct the L3 state or generate/verify proofs, maintaining the core tenet of verifiability crucial for rollup security.
3.4 Native Centralized Limit Order Book (CLOB)
A core component operating within the Catenary L3 execution environment is the native Centralized Limit Order Book (CLOB). Unlike DEXs using AMMs or hybrid off-chain components, Catenary's CLOB logic and order book state reside directly and entirely within the L3 state. This "native" implementation on a high-performance L3 allows Catenary to offer a trading experience and capabilities akin to traditional financial exchanges while retaining the benefits of a decentralized infrastructure (specifically, censorship resistance and verifiable state rooted in the L1/L2).
The Catenary CLOB features:
- Order Book Management: An on-chain data structure (optimized for the L3 environment) efficiently stores buy and sell limit orders, organized by price level and time priority within each level.
- Matching Engine: The core logic of the CLOB is the matching engine. It continuously scans the order book for matching buy and sell orders. Catenary's matching engine operates based on standard financial market principles, typically Price-Time Priority (PTP), where orders at the best price are matched first, and among orders at the same price, the earliest orders are matched first. The matching engine is designed for high throughput within the L3, enabling rapid order placement, modification, cancellation, and execution.
- Order Types: Support for standard order types relevant to financial trading, such as Limit Orders and Market Orders, is fundamental. More advanced order types (e.g., Stop-Loss, Fill-or-Kill) can be implemented at the L3 application layer.
- Performance: By operating natively within the L3, the CLOB benefits from the optimized execution environment, lower latency (targeting sub-second transaction confirmation times within the L3, see Section 6.2), and custom gas economics. This enables the rapid state updates required for a responsive order book and efficient trade execution.
- Capital Efficiency: A CLOB architecture can be more capital efficient for concentrated liquidity compared to AMMs, especially for stable pairs or assets with well-defined price expectations, potentially contributing to tighter bid-ask spreads (see Section 6.4).
The native CLOB is the primary venue for asset exchange within Catenary, providing the liquidity necessary for the settlement of trades initiated through various means, including potentially those facilitated by the Geass Intent Logic.
3.5 The Mobius Sybil Agentic Council (MSAC): Heterogeneous Interoperability Layer
A pivotal element enabling Catenary's ambition to bridge decentralized financial markets with traditional and state-owned financial infrastructure is the MSAC. Distinct from the core L3 rollup execution, MSAC functions as a sophisticated, potentially semi-autonomous layer specifically engineered for managing complex interactions across heterogeneous systems. As demonstrated by performance simulations (Section 6.6), MSAC is designed to handle a significant volume of requests concurrently and exhibits throughput characteristics capable of matching demanding upstream loads (e.g., 20 RPS) from the Catenary L3. Its primary technical purpose is to serve as an intelligent middleware and secure gateway for seamless protocol translation, data exchange, and transaction coordination between the Catenary L3 environment and diverse external endpoints, including traditional banking APIs, legacy payment systems, government databases, and other distributed ledgers.
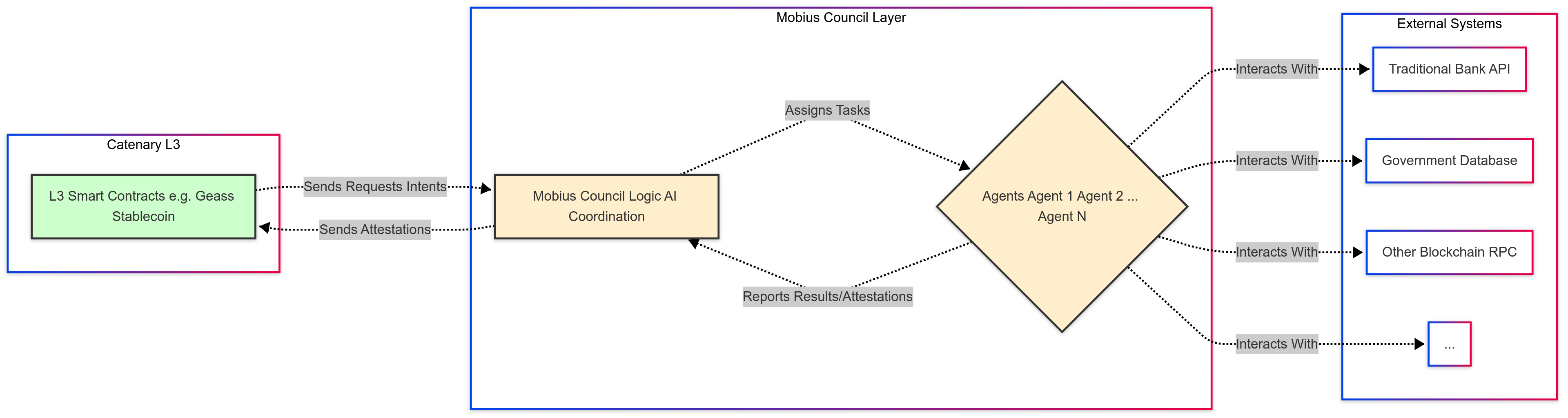
The Mobius Sybil Agentic Council is conceived as a distributed system comprising multiple specialized software agents coordinated by Geass. While the detailed internal architecture of the Council is a subject of ongoing development and will be elaborated further in subsequent work or appendices, its core technical function relies on:
- Autonomous Agents: Individual agents are designed to handle specific types of external system interactions or data processing tasks (e.g., an agent for SWIFT communication, an agent for querying a specific government land registry API, an agent for interacting with another blockchain's RPC endpoint). These agents encapsulate the necessary protocols and authentication mechanisms for their target systems.
- Council Coordination Logic: Geass acts as an orchestrator for the autonomous agents. It receives requests (often originating from intents on the L3), determines the appropriate sequence of agent actions required, assigns tasks to available agents, monitors execution progress, handles failures and retries, and aggregates results. This logic may apply principles of intelligent decision-making and coordination found in multi-agent systems to optimize task allocation and resource usage.
- Secure Integration with Catenary L3: The MSAC interacts with the Catenary L3 through well-defined, secure interfaces, likely involving dedicated smart contracts on the L3. Cryptographic mechanisms are used to ensure the integrity and authenticity of communication (e.g., agents signing attestations about external events, L3 contracts verifying these signatures).
- Protocol Translation and Data Handling: A core technical challenge addressed by MSAC is the significant disparity in communication protocols (e.g., REST APIs, SOAP, FIX, proprietary formats), data formats (JSON, XML, binary), and operational paradigms between the blockchain world and traditional systems. MSAC agents perform the necessary translation and data mapping to enable meaningful communication.
The Mobius Sybil Agentic Council is critical for features such as Effortless On/Off-Ramping (Section 8.1) and Frictionless Asset Tokenization (Section 8.3). While MSAC operates off-chain relative to the core Catenary L3 execution, its interactions and outcomes relevant to L3 state changes must be provable or verifiable on-chain where possible, ensuring the overall integrity of the system. The specific trust model and verification mechanisms for Mobius's interactions will be detailed in Section 7.4 (Security).
4 Core Protocols
Beyond the underlying layered architecture, Catenary's functionality is governed by core protocols designed to optimize user experience, guarantee settlement, and align network participant incentives. This section details the Geass and the Proof-of-Liquidity mechanism.
4.1 Geass
The Geass serves as Catenary's intent coordination layer, abstracting away the complexities of explicit transaction execution and enabling users to declare their desired outcomes ("intents"). This paradigm shift from specifying how to specifying what is particularly powerful in a cross-border financial context involving potential interactions with off-chain systems via MSAC, disparate liquidity sources (the native CLOB, potential external pools), and various asset types.
Technically, an Intent in Geass is a signed message specifying a desired future state or outcome, subject to certain constraints. An Intent message structure can be formally represented as a data structure:
I = {UserAddress, DesiredOutcome, Constraints, Expiry, Nonce, Signature}Where:
UserAddress: The address of the user submitting the intent.DesiredOutcome: A high-level description of the user's goal (e.g., "exchange 1000 USDC for ZAR stablecoin", "settle invoice #XYZ with ABC entity"). This is often encoded in a structured format understood by the Geass Engine.Constraints: Conditions under which the user is willing to accept the outcome (e.g., minimum exchange rate, maximum fee, specific counterparties allowed, required external data attestations).Expiry: Timestamp or block number after which the intent is invalid.Nonce: Value to prevent replay attacks.Signature: Cryptographic signature over the intent message, verifying authenticity and authorization.
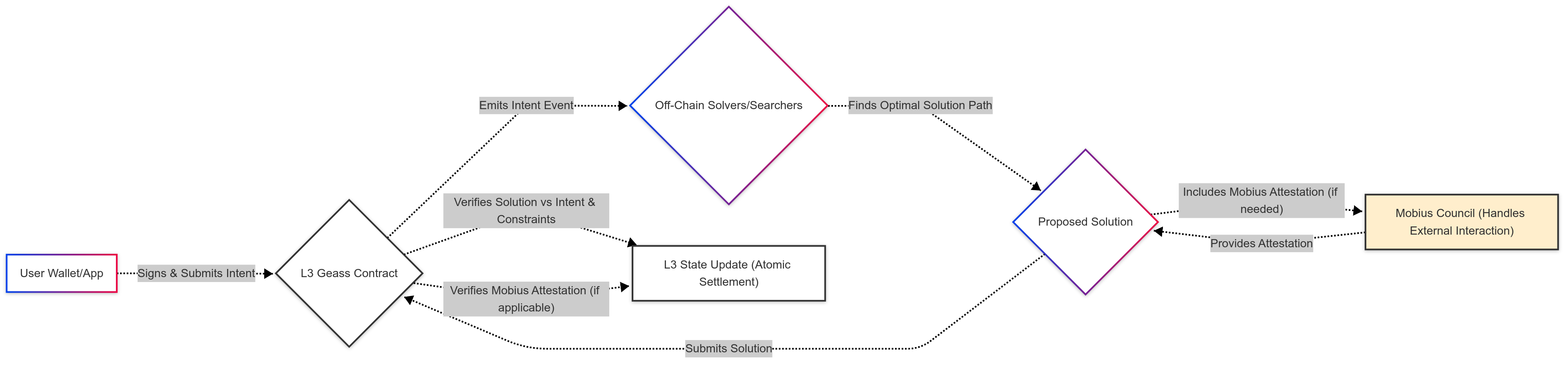
Geass is a logical component (implemented partially on-chain via smart contracts on the Catenary L3 and potentially with off-chain searchers/solvers) responsible for Intent Discovery, Validation, Matching, Solution Finding, Execution, and Settlement Guarantee. Solution Finding can be framed as a mathematical optimization problem, where a solver searches for an optimal execution path S that fulfills an Intent I while maximizing a defined objective function f(S) subject to technical and user-defined constraints C(S,I):
Maximize f(S)
Subject to C(S,I) are satisfied
The objective function f(S) could represent factors such as minimizing transaction cost, maximizing execution price for swaps, or maximizing aggregate surplus when batching multiple intents. The constraints C(S,I) include ensuring the resulting state change matches the DesiredOutcome, all user-specified Constraints are met, and the solution path is technically executable and verifiable (e.g., confirming required external actions via Mobius attestations). The formal definition of the solution space S and the function f(S) is application-specific and critical for the Geass Engine implementation.
A key aspect is the seamless integration of off-chain solution finding with on-chain settlement guarantees. Searchers or solvers computationally derive solutions off-chain, but the final, trustless verification and execution occur via the Geass smart contracts on the L3. These contracts are responsible for cryptographically verifying that a proposed solution S accurately fulfills the original intent I according to its specified parameters and constraints before any state changes (like asset transfers) are executed on the L3 atomically, providing guaranteed settlement on the L3 upon transaction confirmation. This ensures that even if external systems or off-chain components are involved in the solution path (mediated by MSAC), the final asset transfer or state change on the Catenary L3 is cryptographically guaranteed once confirmed on the L3 and subsequently finalized via the Base L2 + ZK proof mechanism.
Geass intent-based approach streamlines complex financial operations into simple declarations for users, while leveraging the power of competitive off-chain computation to find optimal execution paths, ultimately settling on the transparent and verifiable Catenary L3.
4.2 The Proof-of-Liquidity (PoL) Mechanism
Reliable and deep liquidity is paramount for any functional financial market infrastructure, enabling efficient price discovery and low-slippage trading. In traditional finance, market makers are incentivized through various means (spread capture, rebates). In a decentralized environment, explicit mechanisms are required to incentivize market participants to contribute liquidity consistently and effectively. Catenary moves beyond implicit incentives (like AMM fees) and utilizes a more explicit Proof-of-Liquidity (PoL) mechanism.
The PoL mechanism in Catenary is a protocol designed using principles from mechanism design to formally define, measure, verify, and reward the provision of valuable liquidity to the network. Its primary objective is to align the incentives of liquidity providers (LPs) and service providers with the network's goal of fostering deep, stable, and accessible markets.
Defining and Measuring Liquidity:
In the context of Catenary's PoL, "liquidity" is technically defined and measured by metrics like Order Book Depth, Spread, and Order Uptime. A participant's cumulative "Proven Liquidity" score over a period T is calculated using a formal mathematical formula. A representative simplified form, as used in our simulation analysis (Section 6), integrates contributions over time based on weighted metrics:
ProvenLiquidity_i(T) = ∫[t₀ to t₀+T] (w_D ⋅ Depth_i(t) - w_S ⋅ Spread_i(t) + w_U ⋅ UptimeIndicator_i(t)) dtWhere:
ProvenLiquidity_i(T): Cumulative score for participantiover[t0, t0+T].Depth_i(t): Metric for liquidity depth provided by participantiat timet(e.g., total volume within a percentage of mid-price).Spread_i(t): Metric for the tightness of participanti's bid-ask spread at timet(lower is better, hence the negative weight).UptimeIndicator_i(t): Binary indicator,1if participantiis actively providing liquidity at timet,0otherwise.w_D, w_S, w_U: Configurable non-negative weighting coefficients. The simulation usedw_D=0.5, w_S=0.2, w_U=0.3.
Incentive Structure:
Participants wishing to earn PoL rewards must stake native Catenary tokens (or potentially other designated assets). Rewards are then distributed from a predefined pool proportionally based on a participant's cumulative proven liquidity score over a given period. The formula for reward distribution per participant i for a period T from a total pool TotalRewards_T is:
Rewards_i = TotalRewards_T × (ProvenLiquidity_i(T) / Σ[j] ProvenLiquidity_j(T))Where Σ[j] ProvenLiquidity_j(T) is the sum of scores for all participants j over the period.
Slashing Conditions:
Penalties are applied for detrimental behavior that harms market quality. A primary example is prolonged downtime. Continuous downtime exceeding MaxDowntimeAllowed triggers a penalty. A slashing penalty on staked collateral StakedAmount_i for participant i can be formalized as:
Penalty_i = SlashingPercentage × StakedAmount_iWhere SlashingPercentage is a predefined rate applied when a slashing condition is met (e.g., 10% in the simulation). Other conditions, like consistently providing excessively wide spreads or manipulating metrics, could also trigger penalties.
Simulation and Analysis:
To validate the effectiveness of the PoL mechanism and its incentive alignment, a simulation was conducted modeling the behavior of four participants with varying liquidity provision strategies over 100 time units (see Section 6 Performance for simulation details). The simulated results (Table 1) demonstrate that the calculated Proven Liquidity score effectively differentiates participants based on the quality and consistency of their liquidity provision according to the defined metrics (Depth, Spread, Uptime) (see Figure 5). Participants modeling higher average depth and lower average spread consistently achieved higher Proven Liquidity scores and subsequently received the largest shares of the rewards (Table 1). Rewards were distributed in direct proportion to each participant's cumulative Proven Liquidity score, validating the core incentive mechanism.
The simulation successfully triggered the slashing mechanism: Participant 4, programmed with a period of downtime exceeding the defined MaxDowntimeAllowed threshold (5 units), incurred a 10% slashing penalty on their stake at time t=46. This demonstrated the protocol's enforcement of uptime requirements.
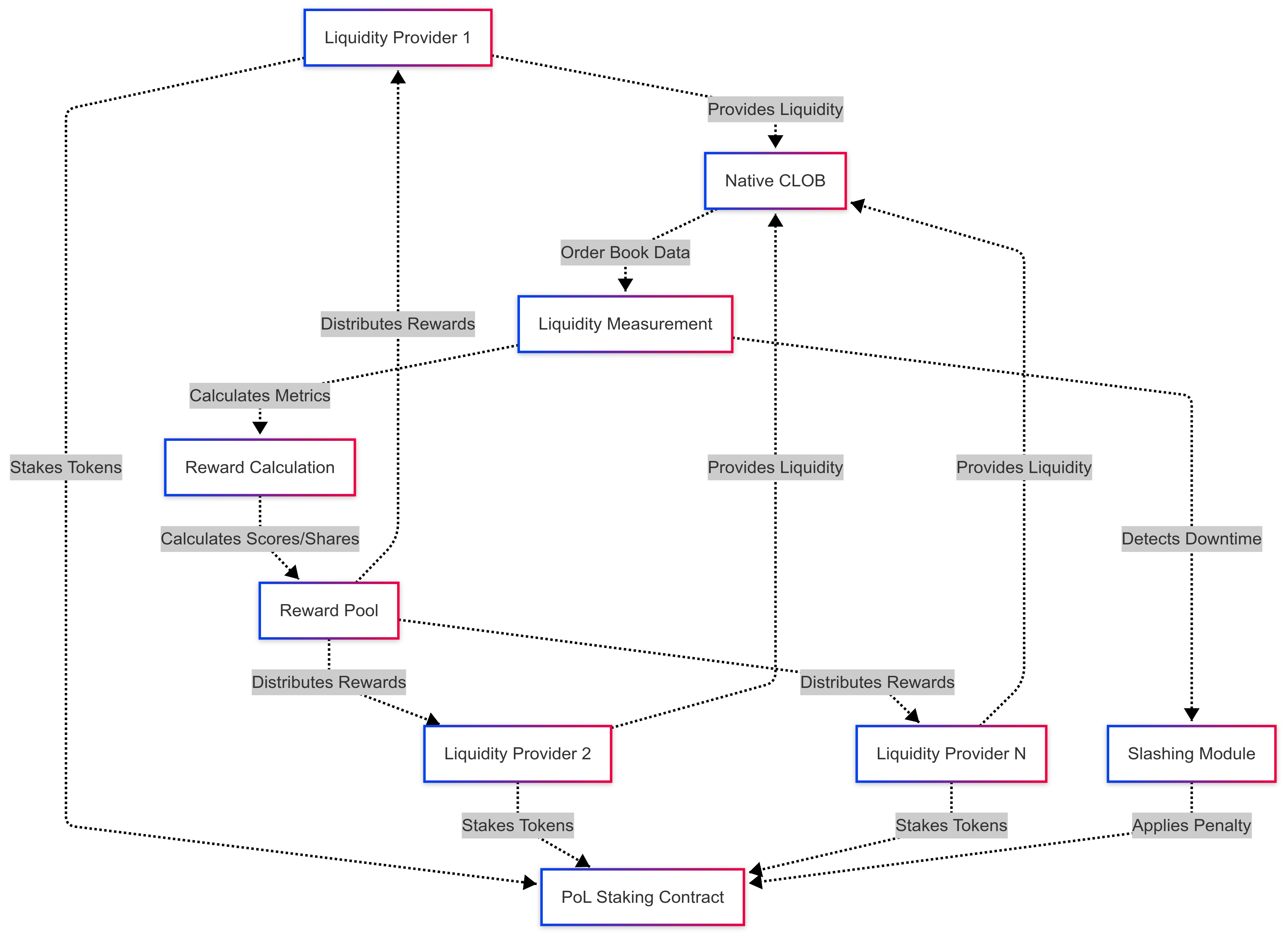
Table 1: PoL Simulation Results Summary
| Participant ID | Initial Stake | Final Stake | Total Proven Liquidity (T) | Reward Share | Calculated Rewards | Avg Depth | Avg Spread | Avg Uptime |
|---|---|---|---|---|---|---|---|---|
| 1 | 10000 | 10000.00 | 5053.65 | 0.3589 | 358.85 | 100.48 | 0.0098 | 1.00 |
| 2 | 10000 | 10000.00 | 3048.98 | 0.2165 | 216.50 | 60.40 | 0.0500 | 1.00 |
| 3 | 5000 | 5000.00 | 1017.90 | 0.0723 | 72.28 | 19.80 | 0.0976 | 1.00 |
| 4 | 12000 | 10800.00 | 4962.30 | 0.3524 | 352.36 | 110.31 | 0.0144 | 0.90 |
Table 2: Correlation Matrix from PoL Simulation
| Metric | Avg Depth | Avg Spread | Avg Uptime | Total Proven Liquidity (T) | Calculated Rewards |
|---|---|---|---|---|---|
| Avg Depth | 1.000000 | -0.986058 | -0.605213 | 0.992570 | 0.992570 |
| Avg Spread | -0.986058 | 1.000000 | 0.468256 | -0.998375 | -0.998375 |
| Avg Uptime | -0.605213 | 0.468256 | 1.000000 | -0.503855 | -0.503855 |
| Total Proven Liquidity (T) | 0.992570 | -0.998375 | -0.503855 | 1.000000 | 1.000000 |
| Calculated Rewards | 0.992570 | -0.998375 | -0.503855 | 1.000000 | 1.000000 |
A correlation analysis based on the simulation results (Table 2) further confirms the strong relationship between liquidity metrics and outcomes. A strong positive correlation (0.99) was observed between average Depth and both the total Proven Liquidity score and calculated Rewards. A strong negative correlation (-0.99) was found between average Spread and the score/rewards. Average Uptime showed a moderate negative correlation (~ -0.50) in this scenario, illustrating the multi-faceted nature of the score and the relative weighting of factors in this specific simulation scenario. The simulation validates the intended proportionality between Proven Liquidity and reward distribution, showing a perfect correlation of 1.00 between the two outputs (Table 2).
Mechanism Design Principles:
The PoL mechanism, validated by simulation, is designed to be Sybil-resistant (staking costs), incentive-compatible (rewards tied to verifiable metrics), and robust (penalties deter detrimental behavior). By directly rewarding measurable contributions to market quality, PoL aims to cultivate a more stable and efficient liquidity landscape than purely implicit incentive models.
5 Programmable and Stable Digital Currencies
Efficient and reliable value transfer is fundamental to Catenary's mission of accelerating cross-border trade settlement. While Catenary facilitates the trading and settlement of various assets on its native CLOB, a need exists for stable units of account and mediums of exchange, particularly for cross-currency transactions and the eventual representation of local currencies. Catenary addresses this through the introduction of programmable, stable digital currencies, designed for resilience and deep integration within the network's protocols, including Geass.
5.1 Technical Design Philosophy: Diversified, Transparent Reserves
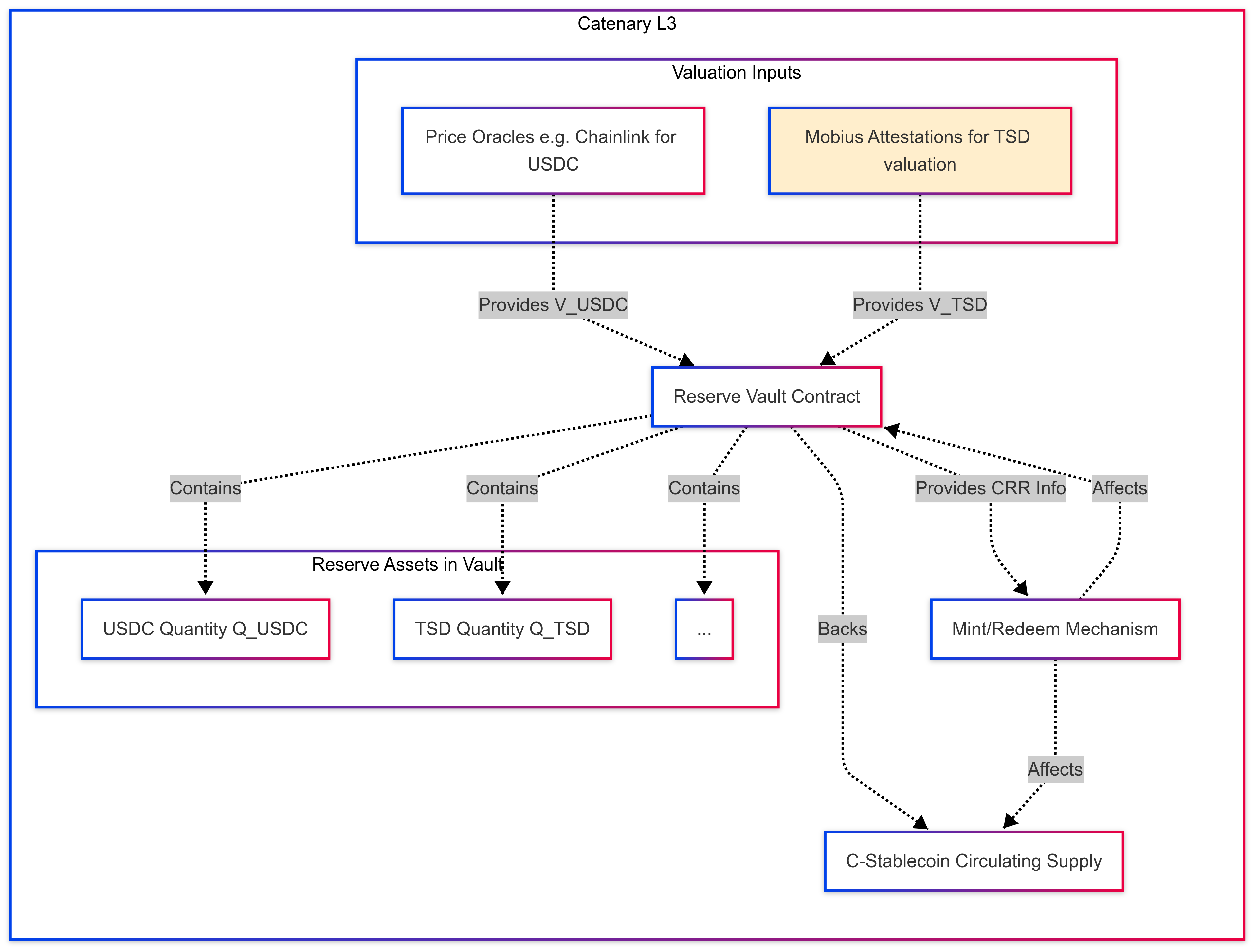
The stable digital currencies issued on Catenary (referred to herein as C-Stablecoins, potentially including representations of major currencies like USD and potentially tokenized local currencies) are designed primarily as reserve-backed stablecoins with potential algorithmic enhancements for stability management. The core principle is to maintain a high level of transparency and verifiability regarding the underlying reserve assets, while leveraging the Catenary L3's programmability. The reserve is held in a collection of smart contracts on the Catenary L3 (and potentially associated vaults on underlying layers or external systems integrated via MSAC). These reserves are diversified across multiple asset classes to mitigate single-point failure risks.
5.2 Reserve Composition and Management
The reserve backing C-Stablecoins is technically structured to include:
- Major Digital Dollar Stablecoins: Highly liquid and reputable stablecoins such as USDC and USDE (if integrated) are held as a significant portion of the reserve. Technical integration involves audited mechanisms to represent these assets securely on the Catenary L3.
- Tokenized Sovereign Debt Instruments (TSDs): A key innovation is the inclusion of tokenized sovereign debt instruments from supported nations within the reserve. This component provides diversification and facilitates potential 'Dollarization easing' by creating stablecoins partially backed by local assets.
Technical Process of Tokenization:
The process of incorporating sovereign debt involves technically representing these off-chain assets as tokens on the Catenary L3. This requires a robust and verifiable tokenization process:
- Verification of Off-Chain Asset: Existence, ownership, and key characteristics (e.g., maturity, coupon rate) must be verified in the traditional legal and financial system.
- Mobius Sybil Agentic Council Integration: This verification and ongoing monitoring is where MSAC plays a critical role. MSAC agents interact with external databases or APIs (e.g., central bank registries, custodian reports) to confirm asset details and provide secure, signed attestations (as discussed in Section 3.5 and 8.3).
- On-Chain Representation (Minting): Upon successful on-chain verification of MSAC attestations by L3 smart contracts, Tokenized Sovereign Debt (TSD) tokens are minted on the Catenary L3, representing verifiable claims on the underlying assets. These tokens could conform to standards like ERC-1155 or a custom L3 standard.
- Reserve Vaulting: The minted TSD tokens are deposited into designated reserve vault smart contracts on the Catenary L3.
- Ongoing Attestation/Verification: MSAC agents may provide periodic attestations to the L3 verifying the continued status of the underlying assets, influencing TSD valuation within the reserve (as assumed in the valuation model for simulation).
The smart contracts managing the reserve vaults are publicly auditable on the Catenary L3, providing transparency into the reserve composition and the Reserve Coverage Ratio (CRR). The CRR at time t is formally defined as:
CRR(t) = (Σ[k ∈ Reserves] Q_k(t) ⋅ V_k(t)) / S(t)Where:
CRR(t): Reserve Coverage Ratio at timet.Reserves: Set of reserve assetsk.Q_k(t): Quantity of reserve assetkheld in reserve vaults at timet.V_k(t): Market value of one unit of reserve assetkat timet. This is determined via secure oracles for liquid digital assets and a defined, potentially Mobius-attested, valuation methodology for assets like TSD (as used in simulation).S(t): Total circulating supply of C-Stablecoins at timet.
5.3 Stability Mechanism
Maintaining the price peg (e.g., P_peg = 1.00 USD) relies on a combination of overcollateralization (ideally CRR ≥ 1.0), arbitrage mechanisms, and protocol-managed stability operations.
- Arbitrage: The primary peg stabilization relies on decentralized arbitrageurs motivated by profit opportunities when the C-Stablecoin market price
P_CS(t)deviates from the pegP_peg. Profit for arbitrageurs who buy below peg and redeem is modeled as:Profit_Redeem(t) = max(0, (P_peg ⋅ min(1, CRR(t)) - P_CS(t)) ⋅ (1 - TxnCost_Redeem)) - Profit for those who mint (by depositing reserve assets equivalent to
P_peg) and sell above peg is modeled as:Arbitrageurs execute trades or mint/redeem operations when these profits exceed a threshold, pushingProfit_MintSell(t) = max(0, (P_CS(t) - P_peg) ⋅ (1 - TxnCost_MintSell)) if CRR(t) ≥ 1P_CS(t)back towardsP_peg. - Protocol-Managed Operations: The protocol may employ mechanisms like adjusting mint/redeem fees dynamically based on CRR or market conditions, or actively managing reserve composition (e.g., selling volatile assets during stress) to bolster stability.
- Reserve Valuation: Accurate and timely valuation of
V_k(t)is critical for CRR calculation and effective arbitrage, relying on secure oracles and robust TSD valuation methods (potentially attested by Mobius).
Simulation and Analysis of Reserve Stability:
To quantitatively assess the stability mechanism's resilience, a simulation was conducted modeling the C-Stablecoin dynamics over 200 time units (see Section 6 Performance for simulation details). The simulation included a diversified reserve (USDC and volatile TSD) backing the supply and incorporated asset volatility (including a 40% TSD price drop stress event at t=100) and market-driven arbitrageur behavior.
The simulation results validate that the arbitrage mechanism actively works to stabilize the C-Stablecoin price around its peg under normal operating conditions and reacts to deviations caused by market noise or reserve volatility (see Figure 8).
 over time).png)
The stress event at t=100 presented a significant test, causing an immediate and sharp decline in the CRR (to a minimum of 0.8674) and a notable de-pegging of P_CS (dropping to a minimum of 0.9348). Critically, the simulation showed that the arbitrage mechanism remained active even when the system was under-collateralized and the peg was broken, as long as the redemption value (P_peg * min(1, CRR)) was still higher than the market price (P_CS) after accounting for costs. Significant redemption volume was observed immediately following the stress event (see Figure 9), contributing to the recovery of the peg by reducing supply and creating buying pressure.
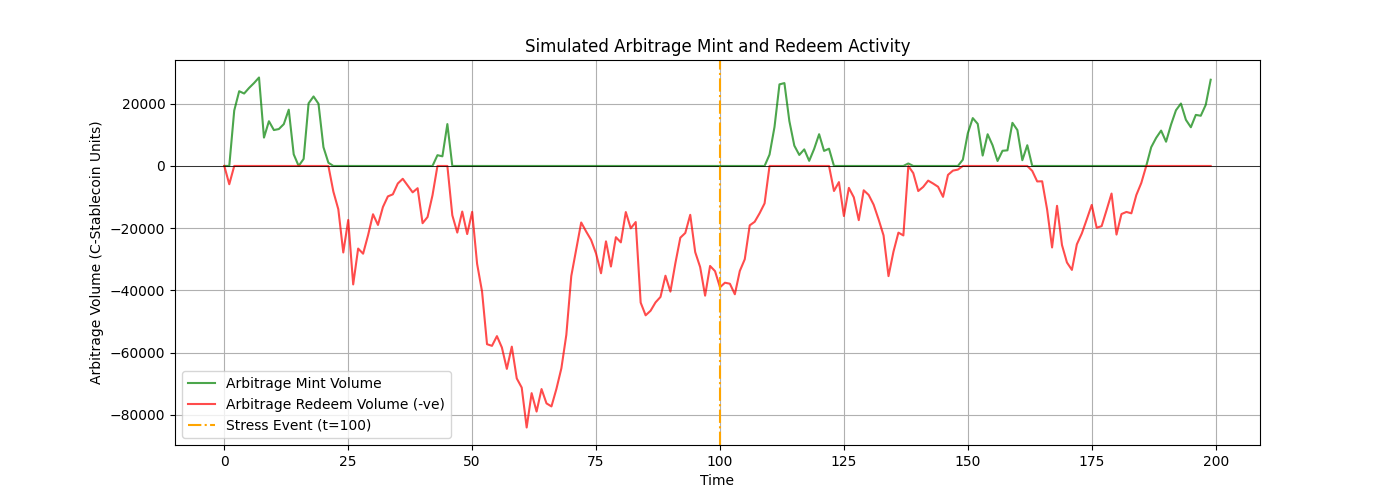
Over the subsequent period, both P_CS and the CRR showed signs of recovery, with the CRR increasing back to 1.0147 by the end of the simulation. While the system spent significant time deviating from the peg (e.g., 91.5% of the simulated time > 1 cent deviation), illustrating that recovery takes time, the mechanism demonstrated resilience. The simulation also revealed a shift in the reserve composition, with USDC making up a larger percentage (55.3%) of the final reserve value compared to TSD (44.7%), suggesting the redemption process acted as a deleveraging mechanism, shedding some of the asset most impacted by the stress. These results validate the core design principle: a diversified, verifiable reserve and robust arbitrage provide significant resilience against reserve asset volatility.
5.4 Programmability
C-Stablecoins are designed as native tokens on the Catenary L3, likely adhering to extended ERC standards (e.g., ERC-20 with potential extensions for compliance or programmability features). This makes them fully programmable within Catenary's smart contract ecosystem, enabling integration into Geass Intents, automated payment streams, escrow services, and future DeFi applications built on Catenary (as discussed in Section 8.4, 8.5).
6 Performance Benchmarking and Analysis
High performance, encompassing throughput, low latency, rapid settlement, and cost-efficiency, is a non-negotiable requirement for a financial market infrastructure intended to replace or augment traditional systems. This section analyzes the expected performance characteristics of the Catenary network, deriving projections from its architectural design and core protocols, and presenting findings from simulation models.
The simulation model for L3 performance was designed to project Catenary's throughput, latency, and cost under various transaction loads, based on parameters including L3 processing capacity (simulated limit of 500 TPS), 10-second batching to Base L2, EigenDA data availability, and ZK proofs for accelerated L2 finality. The MSAC simulation focused on end-to-end latency and throughput when interacting with external systems.
6.1 Throughput (Transactions Per Second - TPS)
The Catenary L3 architecture, being application-specific and leveraging off-chain computation with efficient data posting via EigenDA, is designed to achieve significantly higher throughput than general-purpose L1s or L2s. The simulation results validate this potential. Under transaction arrival rates up to the configured L3 processing capacity (simulated at 500 TPS), the Catenary L3 was able to process transactions at an average rate closely matching the incoming load, indicating efficient handling of volume below saturation. For example, with a constant arrival rate of 150 TPS over a 1-hour simulation, the average processed throughput was 149.95 TPS. When the simulated arrival rate exceeded the L3's configured maximum capacity (e.g., 550 TPS arrival against a 500 TPS limit), the average processed TPS capped out at the L3's maximum processing rate (500 TPS), and a pending transaction queue grew significantly (180,040 transactions over the hour), demonstrating the throughput limit based on L3 processing power.
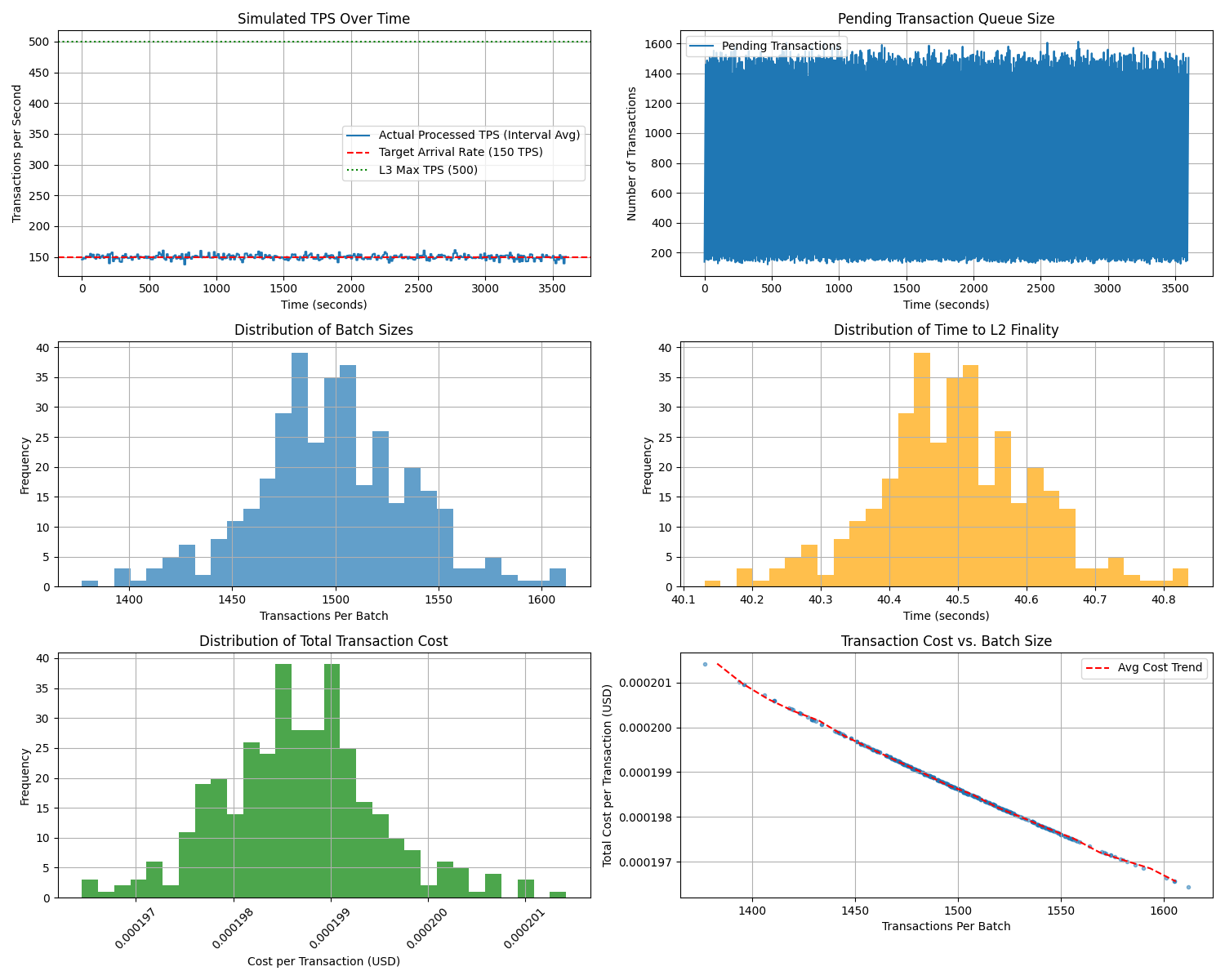
(Note: Figures 10, 11, and 12 refer to subplots within the same combined image generated by the simulation)
This demonstrates that the Catenary L3 can sustain high transaction volumes up to its designed processing limit, free from congestion on underlying layers. The ultimate throughput limit is determined by the L3 sequencer's processing power and the batching parameters.
6.2 Latency
Catenary targets extremely low latency for user-facing interactions within the L3. The architectural design dictates:
- Order Placement/Cancellation: Inclusion in the L3 sequencer's batch is targeted for sub-100 millisecond latency, enabling responsive order book interaction.
- L3 Transaction Confirmation: Once included in a sequenced batch on the L3, transactions achieve probabilistic settlement guarantee with sub-second confirmation latency. This is the latency users experience for basic operations within the Catenary environment.
The pending queue size simulation is an indicator of latency; when the queue is near zero (as observed when arrival rate <= L3 max TPS), transactions are processed almost immediately after arrival, contributing to low confirmation latency.
6.3 Settlement Speed
Catenary provides rapid L3 confirmation and significantly accelerated L2 finality via ZK proofs. The simulation quantifies this acceleration. With a 10-second batching interval, the simulation projected an average time to accelerated L2 finality (T_Batch_L2_Finality) of approximately 40.5 seconds under a 150 TPS load. This time is determined by the batching interval, ZK proof generation time (ZKProofGenerationTime = ZKProofGenerationTime_Base + ZKProofGenerationTime_PerTxn * TransactionsPerBatch), and Base L2 verification time (BaseL2VerificationTime):
T_Batch_L2_Finality = BatchingInterval + ZKProofGenerationTime + BaseL2VerificationTime
(See combined plot image linked in Figure 10)
The simulation showed that the time to L2 finality increases linearly with higher transaction arrival rates (and thus larger batches), impacting ZKProofGenerationTime. At near-maximum load (494 TPS), average L2 finality time was approximately 51 seconds. Even at high load, this remains dramatically faster than the typical multi-day optimistic rollup finality, providing strong settlement assurance suitable for financial markets much more quickly.
6.4 Capital Efficiency
Catenary's technical design enhances capital efficiency in several ways:
- Native CLOB: Allows for precise liquidity provision via limit orders, avoiding impermanent loss issues of AMMs for matched trades and potentially leading to tighter spreads and better price execution for market makers.
- Fast Settlement: Faster settlement times (especially the accelerated L2 finality) mean capital is tied up for shorter periods, reducing counterparty risk duration and freeing up capital for other uses more quickly.
- Proof-of-Liquidity (PoL): Directly incentivizes the efficient deployment of capital as high-quality liquidity (see Section 4.2), rewarding depth and tight spreads rather than just volume locked.
6.5 Cost Efficiency
Catenary's architecture is designed for low operational costs via application-specific L3 gas, EigenDA, and batching. The total cost per transaction (Cost_txn) includes L3 execution and amortized L2/DA/ZK costs per batch:
Cost_txn = Cost_L3_Execution + (Cost_Base_Batch_Submission + Cost_EigenDA_Data + Cost_ZK_Proof_Verification) / TransactionsPerBatchWhere Cost_EigenDA_Data = BatchDataSize * EigenDARate. With simulated parameters (150 TPS load, 10s batching, 0.05 Gwei L2 gas, 0.001 Gwei L3 gas, 0.75 USD/MB EigenDA, 2000 USD/ETH), the average total cost per transaction was calculated to be extremely low, approximately $0.000199 USD.

(See combined plot image linked in Figure 10)
The simulation's sensitivity analysis confirmed that the average cost per transaction decreases significantly as the transaction arrival rate (and thus average batch size) increases (see Figure 12, right panel, and Table 3). This validates the cost-efficiency of batching, as fixed batch costs are amortized across more transactions. The cost levels off at higher rates as per-transaction L3 execution and data costs become more dominant relative to amortized fixed costs.
Table 3: L3 Sensitivity Analysis Results (Varying Arrival Rate)
| ArrivalRate (TPS) | AvgActualTPS | AvgBatchSize | AvgFinalityTime (s) | AvgCostPerTxn (USD) | FinalQueueSize |
|---|---|---|---|---|---|
| 50.0000 | 49.8483 | 498.4833 | 37.4955 | 0.000319 | 0 |
| 105.5556 | 105.3556 | 1053.5556 | 39.1607 | 0.000229 | 0 |
| 161.1111 | 161.1872 | 1611.8722 | 40.8356 | 0.000196 | 0 |
| 216.6667 | 216.8206 | 2168.2056 | 42.5046 | 0.000179 | 0 |
| 272.2222 | 272.1000 | 2721.0000 | 44.1630 | 0.000169 | 0 |
| 327.7778 | 327.2922 | 3272.9222 | 45.8188 | 0.000162 | 0 |
| 383.3333 | 383.0061 | 3830.0611 | 47.4902 | 0.000157 | 0 |
| 438.8889 | 438.5928 | 4385.9278 | 49.1578 | 0.000153 | 0 |
| 494.4444 | 494.4650 | 4944.6500 | 50.8340 | 0.000150 | 0 |
| 550.0000 | 500.0000 | 5000.0000 | 51.0000 | 0.000150 | 178580 |
6.6 Performance Considerations for MSAC Interoperability
While the Catenary L3 provides high internal performance, operations requiring interaction with external systems are dependent on the Mobius Sybil Agentic Council and external endpoints. A simulation modeled end-to-end latency and throughput of requests through MSAC at a rate of 20 RPS, interacting with simulated 'Fast' (~0.3s average latency, 1% failure rate) and 'Slow' (~1.5s average latency, 3% failure rate) external systems, with a 1s retry delay.
The simulation results (Table 4) demonstrated that, with sufficient Council concurrency (10) and agent pool (50), MSAC can sustain a throughput matching the incoming request rate (20.00 RPS achieved).
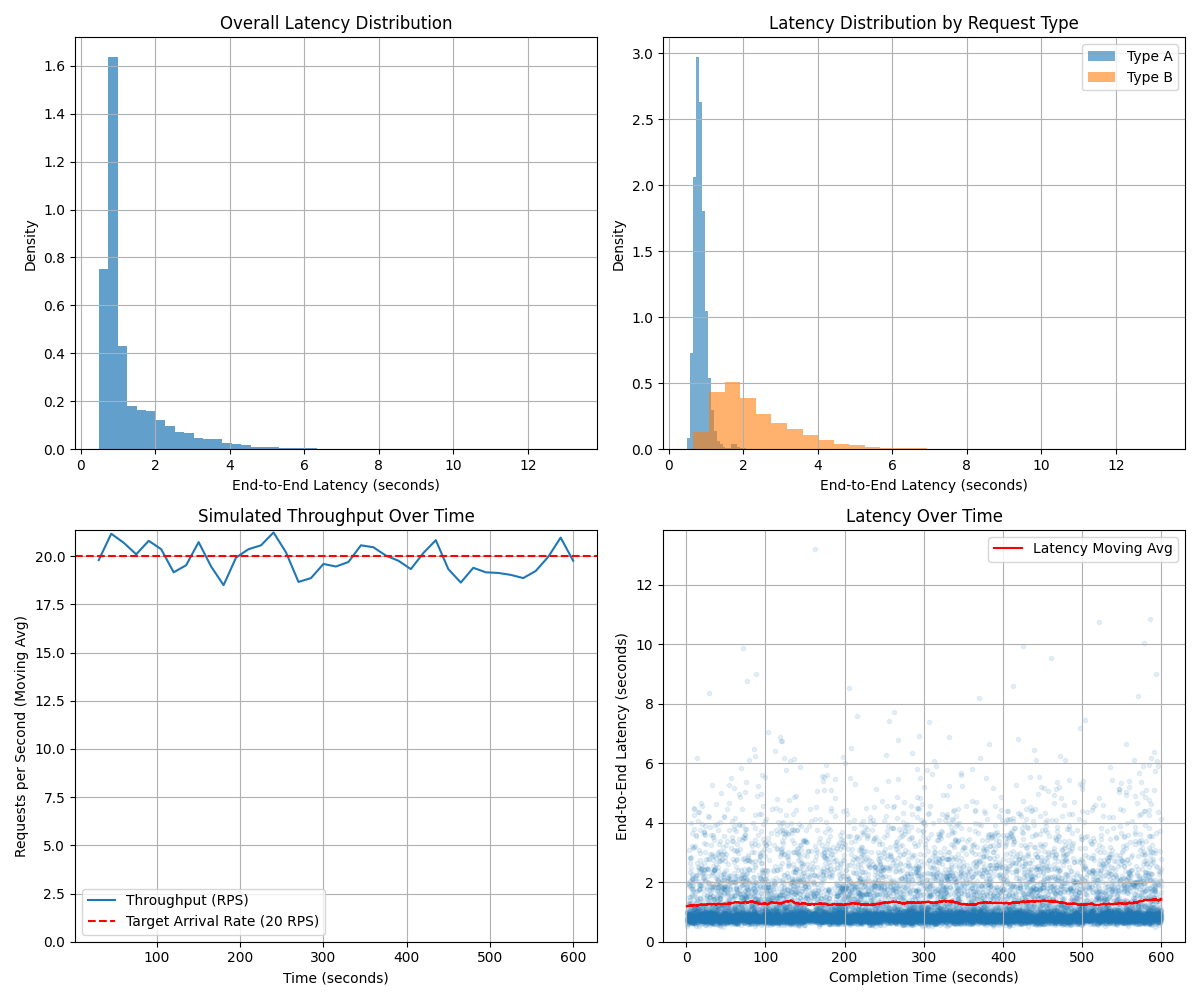
(Note: Figure 13, 14, and 15 refer to subplots within the same combined image generated by the simulation)
The end-to-end latency is significantly influenced by external system performance. The simulation showed an overall average end-to-end latency of 1.283 seconds, with a median of 0.900 seconds. The 95th percentile latency was 3.159 seconds, indicating a right-skewed distribution primarily due to slower external interactions and retries.

(See combined plot image linked in Figure 10)
Latency varied significantly by request type: Type A (Fast External) averaged 0.848s, while Type B (Slow External) averaged 2.304s. External system latency and variability were the dominant factors in end-to-end performance, outweighing MSAC internal processing times. External failures (simulated at 1-3%) impacted latency for affected requests (average 0.017 retries/request) due to the retry delay, although the retry mechanism enhanced overall robustness.

(See combined plot image linked in Figure 13)
Table 4: MSAC Simulation Results Summary
Overall:
- Target Arrival Rate: 20.00 RPS
- Achieved Throughput: 19.81 RPS
- Total Requests Completed: 11884
- Requests still in system: 21
- Latency Avg: 1.299 s
- Latency Median: 0.900 s
- Latency Std Dev: 0.961 s
- Latency Min: 0.488 s
- Latency Max: 13.214 s
- Latency 95th Pctl: 3.348 s
- Avg Retries / Request: 0.017
Latency by Request Type:
| Type | mean (s) | median (s) | std (s) | count | min (s) | max (s) |
|---|---|---|---|---|---|---|
| A | 0.848 | 0.818 | 0.183 | 8310 | 0.488 | 2.878 |
| B | 2.347 | 2.035 | 1.193 | 3574 | 0.660 | 13.214 |
Retry Proportions:
| Retries | Proportion |
|---|---|
| 0 | 0.9837 |
| 1 | 0.0161 |
| 2 | 0.0003 |
In summary, simulations confirm Catenary's architecture enables high throughput, low costs, and accelerated finality for L3 operations. For external interactions via MSAC, performance is bounded by the speed and reliability of integrated traditional systems, although MSACs can sustain the required load and handle external failures gracefully.
7 Security Model and Analysis
The security of the Catenary network is paramount, given its role as a financial market infrastructure handling valuable assets and sensitive transactions. Catenary's security model is based on inheriting the strong cryptographic security of its underlying layers while implementing specific safeguards and mechanisms to address risks inherent in its L3 architecture, application-specific protocols, and heterogeneous interoperability layer.
7.1 Security Inheritance from Layer 1 and Layer 2
Catenary's foundational security is derived from the Ethereum Layer 1 (L1) blockchain, widely regarded as one of the most secure and decentralized public ledgers. By settling its transaction batches to Base Layer 2 (L2), an OP Stack rollup committed to Ethereum security, Catenary benefits from Base's commitment to inheriting Ethereum's security.
The security inheritance mechanism operates as follows: The Catenary L3 sequencer (or potentially a decentralized set of sequencers in the future) submits batches of transaction data and state roots to a verification contract deployed on Base L2. Because Base itself is a rollup that posts data to and verifies proofs on Ethereum L1, invalid state transitions on Base can theoretically be challenged via fraud proofs on L1 (in the standard optimistic model). Catenary's transactions, once settled on Base L2, are indirectly secured by Ethereum's economic finality.
Furthermore, Catenary utilizes Zero-Knowledge (ZK) proofs submitted to Base L2 (as described in Section 3.3) to accelerate the finalization process of L3 batches on L2. The cryptographic validity guaranteed by the ZK proofs means that once a batch's proof is verified on Base, the correctness of the L3 state transition is mathematically confirmed, providing a stronger and faster guarantee of L2 finality than waiting for an optimistic challenge window. This accelerated L2 finality (achieved within seconds/minutes in simulation, see Section 6.3) significantly enhances the security guarantees associated with L3 transactions much sooner.
7.2 Layer 3 Specific Security Considerations
Operating as an application-specific L3 introduces particular security considerations that Catenary's design must address:
- Sequencer Risk: The L3 sequencer is responsible for ordering transactions, executing state transitions, and submitting batches to Base L2. Potential risks include censorship (ignoring user transactions), malicious reordering (MEV extraction), or submitting invalid state roots. Catenary mitigates these through:
- Decentralized Sequencing: A long-term goal is to move towards a decentralized sequencer set to reduce reliance on a single entity.
- Fraud/Validity Proofs: Invalid state roots submitted by a malicious sequencer can be challenged (optimistic model) or are prevented entirely by ZK validity proof verification on L2, using data posted to EigenDA (Section 3.3).
- Forced Inclusions: Mechanisms typically exist in rollup frameworks allowing users to force the inclusion of their transactions via the L2 contract if the L3 sequencer is censoring them.
- State Validity: Ensuring correct state transitions relies on the correct implementation of the L3 execution environment and the verifiability of state roots. ZK proofs (Section 3.3) provide a strong cryptographic guarantee of correct execution. EigenDA (Section 3.3) ensures data availability, allowing independent verification of the state.
- Upgradability Risk: As the L3 software evolves, secure upgrade mechanisms for core smart contracts and sequencer software are essential. Catenary plans to implement transparent governance processes, timelocks for upgrades, and mandatory security audits before deploying changes.
7.3 Security of Core Protocols: CLOB, Geass, and PoL
The core application-level protocols operating within the Catenary L3 require specific security considerations:
- Native CLOB Security: Concerns include order book integrity, fairness of the matching engine, and prevention of manipulation (e.g., wash trading).
- Integrity: Relies on the verifiable L3 state. Tampering with the order book requires compromising the L3 state transition validity, which is protected by the ZK/fraud proof mechanism.
- Fairness: Relies on deterministic matching logic (e.g., Price-Time Priority) implemented transparently in the L3 execution environment and verifiable on-chain.
- Manipulation: Wash trading is disincentivized by transaction fees (even if low) and potentially monitored. The Proof-of-Liquidity mechanism (Section 4.2) incentivizes genuine liquidity provision over manipulative practices. The low latency and small batching window of the L3 mitigate profitable MEV from reordering within a batch compared to slower L1s.
- Geass Security: Ensuring intents are fulfilled correctly and securely, especially when involving off-chain components or external systems via MSAC.
- Intent Integrity and Authentication: Secured by user cryptographic signatures verified on-chain by Geass contracts.
- Solution Validation: This is critical. Geass smart contracts on the L3 perform on-chain validation, verifying that any proposed solution (even if found off-chain or involving Mobius) correctly fulfills the original intent's
DesiredOutcomeandConstraintsbefore executing any atomic state changes (e.g., asset transfers). - Off-Chain Interaction Security: When solutions involve the MSAC, security relies on the secure, verifiable interface between Geass/L3 and MSAC. Geass contracts verify attested confirmations from MSAC regarding external interactions before proceeding with on-chain settlement (detailed in Section 7.4).
- Proof-of-Liquidity (PoL) Security: Preventing Sybil attacks, ensuring accurate liquidity measurement, and implementing secure slashing enforcement.
- Sybil Resistance: Economic Sybil resistance is achieved through the requirement for participants to stake collateral (Section 4.2). The cost of staking makes creating numerous fake identities prohibitively expensive.
- Accurate Liquidity Measurement: Metrics (Depth, Spread, Uptime) must be measured reliably within the verifiable L3 execution environment or via secure, verified data feeds to prevent manipulation by LPs seeking unearned rewards.
- Secure Slashing Enforcement: Slashing conditions (e.g., excessive downtime) are defined in smart contracts. Enforcement requires verifiable evidence (e.g., prolonged downtime detected on-chain based on lack of activity or attested off-chain via a reliable mechanism). The simulation (Section 4.2) successfully demonstrated the technical application of the slashing penalty (
Penalty_i = SlashingPercentage * StakedAmount_i) when a participant violated uptime rules, confirming this enforcement mechanism functions as intended within the protocol logic.
7.4 Security of the Mobius Sybil Agentic Council
The Mobius Sybil Agentic Council introduces interaction with external trust domains (traditional finance, government systems), making its security particularly complex and crucial.
- Internal Council Security: Requires standard robust software security practices for individual agents and a secure, potentially decentralized or fault-tolerant, design for the AI council coordination logic to resist internal manipulation or external attacks. Ensuring integrity relies on cryptographic identification/authentication of agents and secure coordination protocols. Sybil resistance within MSAC, if agents are not strictly permissioned, requires mechanisms like staking or reputation systems within the MSACs layer itself to prevent malicious actors from flooding the system with fake agents.
- Secure Communication with External Systems: Standard security practices like TLS for encrypted channels, proper authentication (API keys, OAuth, certificates), and authorization are necessary when interacting with external endpoints. Protocol adapters within agents must handle potentially malformed or malicious data from external systems robustly.
- Data Integrity and Authenticity from External Systems: This is a major challenge. MSACs agents provide signed attestations to the Catenary L3 confirming the outcomes or data retrieved from external systems. These attestations are verified on-chain (e.g., by Geass contracts) using the agents' registered public keys. The trust model here relies significantly on the integrity of the MSACs process for gathering and attesting to this data. Using multi-agent consensus within MSAC for critical attestations (e.g., requiring confirmation from multiple independent agents interacting with the same external source) can enhance security by increasing the difficulty of forging attestations. Legal and operational agreements with external data providers or system operators are also crucial complementary security layers.
- Secure Handling of External System Unreliability: The Mobius Sybil Agentic Council is designed to manage the inherent unreliability of external systems (downtime, errors). The simulation demonstrated MSAC's capability to manage external system failures through a retry mechanism, successfully completing requests after one or more retries for a small percentage of interactions (average 0.017 retries/request, as discussed in Section 6.6). While retries add latency, they contribute to the robustness of the system by ensuring that transient external issues do not cause outright failure of MSACs-mediated operations. The security implications here involve ensuring that the retry logic itself is robust, does not create new attack vectors (e.g., denial-of-service via repeated failed retries), and does not lead to inconsistent states between the L3 and the external system. Secure logging, monitoring, and potentially circuit-breaker patterns within MSAC are essential.
- Secure Interface with Catenary L3: Interactions between MSAC and the L3 use authenticated calls to specific L3 smart contracts, triggered based on external events confirmed by verified MSAC attestations. Geass plays a key role by validating these attestations against the original user intents before finalizing any on-chain settlement, acting as a final on-chain checkpoint.
The security of MSAC requires a multi-faceted approach blending cryptographic techniques, secure system design (potentially incorporating decentralization within MSAC itself), robust error handling, and strong operational controls and agreements.
7.5 Formal Verification and Audits
Catenary is committed to rigorous security practices. Critical smart contracts (CLOB, Geass, PoL, Stablecoins, L3-MSAC interface) will undergo formal verification where applicable and comprehensive third-party security audits before mainnet deployment and after significant upgrades. The Mobius Sybil Agentic Council design and implementation will also be subject to thorough security reviews, focusing particularly on the interaction points with the L3 and external systems, and the integrity of the attestation mechanisms.
8 Technical Use Cases
Catenary's technical architecture and core protocols are engineered to address the fundamental inefficiencies in existing financial infrastructures, particularly concerning cross-border transactions and asset mobility in regions like Sub-Saharan Africa. This section details key technical use cases enabled by Catenary, illustrating how the layered design, CLOB, Geass, PoL, MSAC, and stable digital currencies interact to deliver novel capabilities.
8.1 Accelerated Cross-Border Trade Clearance and Settlement
The primary technical use case is the radical acceleration and cost reduction of cross-border trade clearance and settlement. Traditional methods are slow (days) and expensive due to multi-hop correspondent banking and legacy systems. Catenary streamlines this process using on-chain (L3) atomic settlement and interoperability with external payment initiation/confirmation systems via MSAC.
Technical Flow Example (e.g., Kenyan Importer paying Nigerian Exporter):
- Intent Formulation (L3): The Kenyan Importer formulates an Intent on the Catenary L3: "Pay Nigerian Exporter ABC [Catenary Address or MSAC-resolvable ID] 500,000 NGN-C Stablecoins from my KES-C Stablecoin balance, conditional on delivery confirmation [could involve MSAC/Oracle data feed]". This Intent (see Section 4.1 for formal structure) specifies the desired outcome, source/destination, amount, and technical constraints (e.g., max slippage on KES-C/NGN-C exchange).
- Geass Resolution (L3/Off-chain): The Geass Engine processes the Intent. It identifies this is a cross-currency payment requiring exchange (KES-C to NGN-C). It searches for the optimal execution path (see Section 4.1 for optimization problem). This could involve executing a swap on the native Catenary CLOB (Section 3.4), finding a multi-hop path leveraging CLOB liquidity and potentially other integrated sources, or evaluating rates to meet constraints.
- On-Chain Execution & Atomic Settlement (L3): Once Geass finds a valid solution (e.g., a series of swaps on the CLOB), it proposes this to the relevant Geass smart contracts on the Catenary L3. The L3 contracts verify the solution's validity against the original Intent. If valid, the contracts atomically execute the necessary token transfers on the Catenary L3 state – debiting the Importer's KES-C, executing swaps (potentially matching against PoL-incentivized orders, Section 4.2), and crediting the Exporter's address with NGN-C. This entire sequence settles near-instantaneously on the L3 (sub-second confirmation, Section 6.2), at very low cost (fractions of a cent, Section 6.5).
- Accelerated Finality (Base L2 + ZK): The batch containing this atomic settlement transaction is included in a batch sent to Base L2. The batch's correctness is rapidly attested by ZK proofs, enabling accelerated L2 finality within minutes (Section 3.3, 6.3), providing strong cryptographic assurance of the settlement far faster than traditional systems.
- External System Confirmation (MSAC - Optional/Conditional): If the Intent included off-chain conditions (e.g., delivery confirmation), Geass could coordinate with the Mobius Sybil Agentic Council (Section 3.5). A MSAC agent would interact with the external system (e.g., shipping company API, customs database). MSAC provides a secure, signed attestation of the data's status to the L3, which Geass verifies as part of the settlement condition (Section 7.4). The latency for this step depends on the external system, as shown in MSAC simulations (Section 6.6).
- Fiat Off-Ramping (Optional, via MSAC): The Exporter can then initiate an off-ramp Intent ("Convert NGN-C to NGN fiat in my bank account X"). This triggers the Mobius Sybil Agentic Council to interact with a Nigerian bank's API (or other payment system) to disburse NGN fiat, debiting the Exporter's NGN-C on L3 upon confirmation from MSAC.
This use case demonstrates how the L3 provides performance, CLOB/PoL provide liquidity, Geass abstracts complexity, ZK proofs accelerate finality, and MSAC enables interaction with external data or fiat rails for streamlined trade.
8.2 Frictionless Asset Tokenization and Trading
Catenary enables the tokenization of diverse traditional assets (e.g., real estate, private equity, sovereign debt), making them tradable on the L3 and unlocking liquidity (as discussed in Section 5.2 for TSDs).
Technical Flow Example (e.g., Tokenizing a fraction of a local Real Estate asset):
- Off-Chain Asset Verification & Structuring: Traditional legal and operational steps occur off-chain to verify ownership, conduct diligence, appraise value, and establish the legal wrapper (e.g., SPV) holding the asset.
- On-Chain Tokenization Intent (L3): A designated entity (e.g., the SPV manager) initiates a tokenization request on Catenary L3, potentially as a Geass Intent, specifying parameters for a new Tokenized Security Object (TSO) token (e.g., total supply representing ownership fractions, link to off-chain property ID).
- MSAC-Mediated Verification: The L3/Geass interacts with the Mobius Sybil Agentic Council (Section 3.5). MSAC agents specialized in relevant external registries (e.g., land registry, corporate registry) provide secure, signed attestations to the Catenary L3, confirming verifiable details from the traditional system (e.g., SPV registration, property title linkage) (Section 7.4). Latency depends on external registry speed (Section 6.6).
- On-Chain TSO Minting (L3): Upon successful on-chain verification of MSAC attestations by L3 smart contracts, the protocol mints the specified number of TSO tokens (e.g., adhering to extended ERC-20/1155 standards) to the entity's address on the Catenary L3.
- Trading on Native CLOB (L3): The minted TSO tokens become available for trading on the native Catenary CLOB (Section 3.4). Users can place limit orders for fractions of the asset. The CLOB's high throughput and low latency (Section 6.1, 6.2), supported by PoL incentives (Section 4.2), enable efficient price discovery and execution for potentially less liquid assets.
- Settlement: Trades of TSO tokens settle near-instantaneously on the Catenary L3 via atomic CLOB matching (Section 3.4), with accelerated L2 finality providing rapid cryptographic assurance of ownership transfer (Section 6.3).
- Ongoing Asset Management (MSAC/L3 Interaction): MSAC can provide ongoing attested data feeds (e.g., rental income distributions, updated valuations) to L3 smart contracts managing the TSO lifecycle (e.g., triggering automated dividend distributions to token holders) (Section 3.5, 7.4).
This use case highlights how Catenary integrates off-chain asset reality (via MSAC) with on-chain representation (TSOs) and trading (CLOB/PoL), unlocking liquidity for assets previously difficult to trade efficiently.
8.3 Programmable Financial Products via Geass and Stablecoins
Catenary's programmable L3 environment, Geass intents, and stable digital currencies enable sophisticated financial products and automated processes beyond simple swaps.
Technical Flow Example (e.g., Automated Micro-Payment Stream using Stablecoins):
- Stream Intent (L3): A user defines an Intent via Geass (Section 4.1): "Pay address B
xamount of C-USD Stablecoin (Section 5) everyinterval(e.g., 1 hour) forduration(e.g., 1 month), starting atstart_time". This intent is authorized via signature and potentially requires locking the total stream amount in an L3 escrow contract managed by Geass. - Geass Scheduled Execution: The Geass Engine identifies this as a recurring Intent and queues it for future resolution at the specified intervals. This scheduling might occur within the L3 state machine or via trusted off-chain keepers interacting with Geass contracts.
- Periodic Resolution (L3): At each interval, the Geass Engine triggers a mini-resolution. It verifies conditions (e.g., current time matches interval, sufficient C-USD balance in escrow).
- Atomic Transfer (L3): Upon successful verification, the Geass smart contract atomically transfers the specified
xC-USD Stablecoins from the escrow contract to the recipient address B on the Catenary L3. This is a standard L3 transaction benefiting from low cost and sub-second confirmation (Section 6.2, 6.5). - Guaranteed Settlement & Finality: The transfer is guaranteed on-chain by the Geass contract's logic and benefits from accelerated L2 finality (Section 6.3).
This use case demonstrates the native programmability of C-Stablecoins within the L3, enhanced by Geass's ability to manage complex, conditional, or scheduled interactions, enabling applications like payroll, subscriptions, or micro-rewards directly on-chain.
These technical use cases illustrate Catenary's capacity to move beyond simple cryptocurrency trading and provide a robust, high-performance foundation for a wide array of financial applications, addressing real-world needs through novel combinations of layered architecture, core protocols, and heterogeneous system interoperability.
9 Discussion and Future Work
Catenary is designed to be a technically advanced, modular financial market infrastructure capable of addressing the long-standing challenges of cross-border trade settlement and financial integration, particularly within Sub-Saharan Africa. By constructing an application-specific Layer 3 network on the OP Stack, we aim to deliver performance, cost-efficiency, and functional depth unattainable on general-purpose Layer 1 or Layer 2 blockchains. The integrated design of core protocols – the native CLOB for efficient trading, Geass for intent-based abstraction and guaranteed settlement, PoL for incentivizing deep liquidity, and the Mobius Sybil Agentic Council for heterogeneous interoperability – represents a novel synthesis of distributed systems, mechanism design, and agentic AI principles applied to financial infrastructure.
The simulation results presented in Section 6 provide quantitative support for Catenary's performance potential. The L3 performance simulation demonstrates the capacity for high throughput (up to the simulated 500 TPS L3 processing limit) and very low transaction costs (average ~$0.0002 USD at 150 TPS), validating the benefits of an application-specific L3 with efficient batching and data availability via EigenDA. The accelerated L2 finality (average 40-51 seconds depending on load), enabled by ZK proofs, significantly reduces settlement risk timeframes compared to traditional optimistic rollups, which is crucial for financial applications. The C-Stablecoin stability simulation illustrates the resilience of the reserve-backed model against volatility, showing how market-driven arbitrage can maintain the peg even under stress (minimum 0.9348 price observed after 40% reserve asset drop), with the reserve composition adapting over time as assets are redeemed. The MSAC simulation highlights that while the MSAC layer itself can sustain the required throughput (20 RPS achieved), the end-to-end latency (average 1.28s, 95th% 3.16s) and reliability of operations involving external systems remain highly dependent on the performance characteristics of those traditional or state-owned infrastructures, emphasizing that technical interoperability must be complemented by robust external system integration and potentially service level agreements.
The intent-based nature of the Geass protocol offers a powerful abstraction layer, simplifying user interaction and enabling sophisticated financial operations by decoupling intent formulation from execution details. This approach allows for potential optimizations by specialized solvers and facilitates complex conditional settlements involving both on-chain and off-chain components mediated by MSAC. The Proof-of-Liquidity mechanism, informed by mechanism design principles and validated by simulation, provides a theoretically sound basis for incentivizing the consistent provision of high-quality liquidity necessary for a functional CLOB and efficient markets for potentially less liquid, long-tail assets. The simulation confirmed the mechanism's ability to distribute rewards proportionally to defined quality metrics (strong correlation with depth/spread) and enforce rules via slashing.
The Mobius Sybil Agentic Council is a particularly innovative component, representing a significant step towards seamless interaction between decentralized networks and legacy or permissioned systems. By employing agentic AI principles, MSAC aims to navigate the technical and operational complexities of diverse external interfaces. However, the successful and secure operation of MSAC requires careful consideration of trust models, agent coordination, verification mechanisms for attestations originating from potentially untrusted external sources, and robust handling of external system failures (as demonstrated by simulation, failures add latency but retries improve robustness). The "Sybil" aspect in its name, while intended to denote multiplicity and coordination, also highlights the theoretical computer science challenge of Sybil resistance; ensuring the integrity and non-malicious behavior of agents and the council within the MSAC system is paramount and relies on cryptographic guarantees, robust protocol design within MSAC itself (potentially involving decentralized verification or staking by agents), and strong operational controls.
Future Work:
Building upon the foundational architecture and protocols described in this paper, several key areas are identified for future research, development, and refinement:
- Formal Verification and Security Audits: Rigorous formal verification of core L3 smart contracts (Geass, PoL, Stablecoins, L3-to-MSAC interface) and comprehensive third-party security audits across the stack are critical next steps before any production deployment.
- Advanced Mechanism Design Refinements: Further research into dynamic PoL parameter adjustments (e.g., adapting weights
w_D, w_S, w_Ubased on market conditions) and designing optimal incentive structures for Geass solvers/searchers is needed to ensure robust performance under varying network states. - Mobius Sybil Agentic Council Architecture and Trust Model Formalization: A deeper technical exposition of MSAC's internal architecture, agent coordination algorithms, specific external interaction protocols, and a formalized trust model for external attestations (potentially involving multi-agent consensus or reputation systems) is required. Research into decentralized AI coordination and verifiable computing for agent attestations is relevant here.
- Empirical Performance Benchmarking: Deploying Catenary on a public test network is necessary to conduct empirical testing and validate simulation projections under real-world network conditions, transaction mixes, and adversarial behavior.
- Zero-Knowledge Proof Integration and Optimization: Detailing the specific ZK proving system chosen (e.g., SNARKs vs. STARKs), optimizing proof generation times and costs, and exploring the potential use of recursive proofs or ZK for selective privacy features are ongoing areas of development.
- Development of Programmable Financial Primitives: Building a library of reusable smart contract modules for common financial operations (e.g., standardized escrow, lending primitives, derivatives) on the Catenary L3 to accelerate application development.
- Governance Model Development: Specifying and implementing the technical mechanisms for decentralized governance, covering aspects like protocol upgrades, parameter adjustments (e.g., PoL weights, stablecoin reserve policies), and dispute resolution processes.
Addressing these areas in future work will be crucial for the continued technical maturation and robustness of the Catenary network, paving the way for its implementation as a foundational infrastructure for accelerated cross-border finance.
10 Conclusion
The persistent inefficiencies in traditional cross-border trade clearance and settlement mechanisms, compounded by the limitations of existing decentralized platforms in meeting the performance and interoperability demands of financial markets, underscore the critical need for novel infrastructure. Catenary addresses this imperative by introducing a modular financial market infrastructure based on a high-performance, application-specific Layer 3 network built on the OP Stack.
This paper has presented the technical architecture and core protocols of the Catenary network. We detailed the advantages of an application-specific L3 for achieving optimized throughput, predictable low costs, and tailored functionality essential for financial applications. The native Centralized Limit Order Book (CLOB) operating within this L3 environment is designed to provide a familiar, efficient trading experience with sub-second transaction confirmation latency. We introduced Geass , an intent-based layer that abstracts transaction complexity and ensures guaranteed settlement on-chain, even for operations initiated off-chain or involving external systems. The Proof-of-Liquidity (PoL) mechanism was presented as a carefully designed incentive structure, informed by mechanism design principles, to foster deep and stable liquidity on the platform.
Furthermore, we elaborated on the design of programmable, stable digital currencies, backed by diversified reserves including tokenized sovereign debt, crucial for facilitating cross-currency exchange and reliable value transfer. A key technical innovation is the Mobius Sybil Agentic Council, an agentic AI system engineered to provide a robust technical gateway for seamless, secure interaction between the decentralized Catenary L3 and heterogeneous external systems, including traditional financial infrastructure and state-owned servers, enabling critical functions like fiat on/off-ramping and verifiable asset tokenization. Accelerated Layer 2 finality, achieved by leveraging Base L2 in conjunction with Zero-Knowledge proofs, provides rapid cryptographic assurance of settlement, significantly reducing counterparty risk timeframes.
Quantitative analysis through simulations validates the potential of this architecture. Simulations of the L3 performance project high transaction throughput (up to the simulated 500 TPS limit) and demonstrate per-transaction costs measured in fractions of a cent (average ~$0.0002 USD), highlighting the efficiency derived from the L3 design, batching, and EigenDA. The L3 simulation also quantified the accelerated L2 finality time (average 40-51 seconds depending on load). Analysis through the PoL simulation shows that the defined metrics and reward structure effectively incentivize liquidity provision and that slashing rules can enforce desired behavior, confirming incentive alignment. The stablecoin simulation demonstrates the resilience of the reserve model and the effectiveness of arbitrage in maintaining the peg (recovering from a 40% reserve value shock), illustrating the system's capacity to recover from stress events and showing how reserve composition can adapt. Simulations of the MSAC performance indicate its ability to handle the required load (20 RPS) while underscoring that end-to-end latency for external interactions is primarily dependent on the performance and reliability of the integrated traditional systems (average latency 1.28s, 95th% 3.16s).
By combining these technical components – a tailored L3 architecture, high-performance CLOB, innovative intent and liquidity protocols, AI-driven heterogeneous interoperability, verifiable stable currencies, and accelerated settlement finality – Catenary establishes a technically sophisticated foundation for a hyper-performant, interoperable, and inclusive financial market infrastructure. This infrastructure is specifically positioned to accelerate cross-border trade clearance and settlement in Sub-Saharan Africa, fostering economic integration and paving the way for a new era of permissionless financial innovation built on robust, verifiable technology.